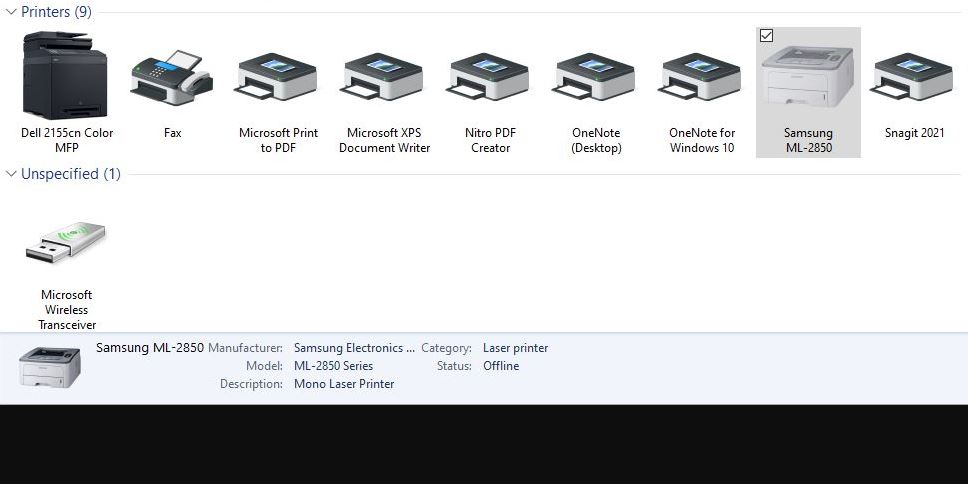
Something odd is still fiddling with my local switch domain. Fortunately, it only affects my office here at Chez Tittel. The usual symptom is that my LAN-attached Samsung ML-2850 shows up in Devices and Printers. But it is grayed out and shows status as offline (see lead-in graphic, middle right and bottom). When that happens bringing offline printers back online requires a specific drill.
How-to: Bringing Offline Printers Back Online
I use Nir Sofer’s great little NetBScanner tool to confirm or establish the IPv4 address the Samsung uses. (Lately, it uses192.168.1.133.) I right-click the offline printer (labeled Samsung ML-2850 in the lead-in graphic). Then I select “Remove device” from the resulting pop-up menu. After that, I must confirm that removal by responding “Yes” to a prompt window that reads “Are you sure you want to remove this device.” Done!
Next, what has been removed gets reinstated. This means clicking “Add a printer” from the top-line menu, then clicking “The printer that I want isn’t listed” when the automated search fails to find the Samsung ML-2850. Next, I click the radio button next to “Add a printer using a TCP/IP address or hostname.” Then I double-check NetBScanner to confirm that the ML-2850’s IP address remains unchanged (aha! It’s moved to …134, so that’s what I enter).
I leave the default “use currently installed driver” option selected and click “Next” again. Then I shorten the printer name to SamML-2850. Because the printer is network-attached, there’s no need to share it (this is required only for USB or other purely device-specific printer connections).
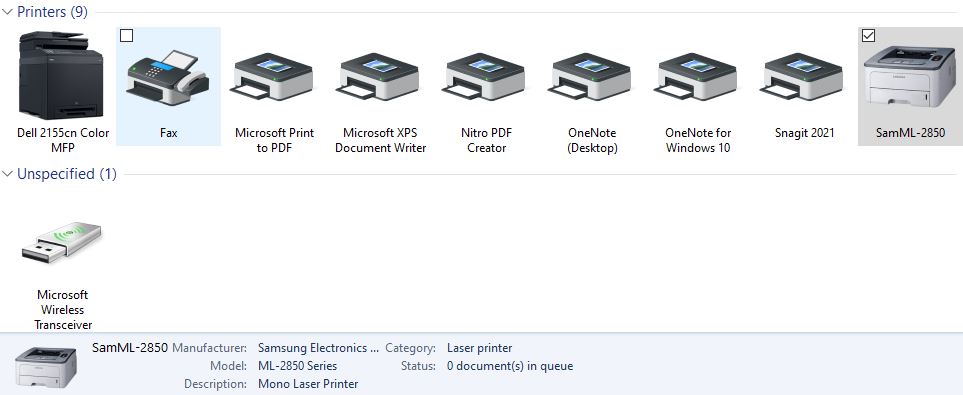
And when I print a test page, Presto! The printer is once again back online. Good stuff!
After removing and re-installing (after double-checking IP address) the Samsung networked printer is back online. Goody!
[Click image for full-sized view]