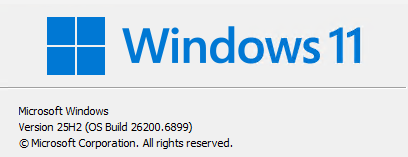
Microsoft’s February 2026 cumulative update, KB5077181, brought most Windows 11 25H2 systems up to build 26200.7840. At least, that’s what I was expecting. But as I rolled out the update across a mix of systems here at Chez Tittel, I noticed something odd. My Lenovo ThinkPads and an ASUS Zenbook A14 quietly updated and rebooted into 26200.7840. The DIY desktop (built on an ASRock motherboard with a Ryzen 5800X) threw a TPM warning and required multiple reboots after a forced cold startup. You guessed it: that one TPM elicits WTF as I must respond to “Update Y/N” for things to proceed.
One TPM Update Elicits WTF, Others Don’t
Let’s unpack what happened. First, the update itself. KB5077181 is a standard cumulative update, but it also includes boot-chain changes that affect Secure Boot and TPM values. On systems with stable firmware and well-behaved TPM implementations, these changes get absorbed quietly. That’s what happened on my Lenovo and ASUS laptops. They rebooted twice and landed on build 26200.7840 without a peep. Copilot tells me that the first reboot is for a servicing stack update, the second for the aforementioned CU.
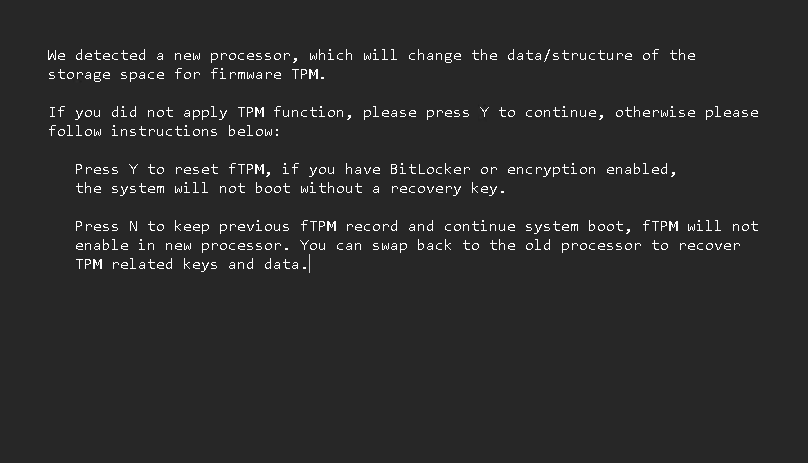
The ASRock-based Ryzen system, aka “Flo6,” had a different reaction. Upon reboot it froze on a black screen. After I cycled power and forced a cold boot, it presented a UEFI-level prompt. That prompt warned about changes to the TPM and Secure Boot configuration, and asked me to enter “Y” to confirm, or “N” to deny. This signals that the Platform Configuration Register 7 (PCR 7) that tracks Secure Boot components has detected a change. The system requires manual confirmation to proceed and reseal the TPM, followed with an additional reboot. But man, is that a cryptic message or what? (It appears as the lead-in graphic above.)
Why this discrepancy? It comes down to platform differences. OEM systems like Lenovo and ASUS laptops benefit from tightly integrated firmware, drivers, and update pipelines. Their UEFI implementations are mature. Also, their TPM and Secure Boot configurations get validated against Microsoft’s updates. Thus, they handle PCR changes gracefully and typically reseal the TPM silently with no user intervention.
The ASRock Difference
ASRock, on the other hand, does things differently. Though their firmware is functional and generally reliable, but it’s not as polished or tightly integrated as enterprise-grade or premium OEM systems. ASRock tends to use more standard, out-of-the-box AMI firmware. It offers only minimal validation for Secure Boot and TPM changes. Combine that with AMD’s fTP (known to be more sensitive to boot-chain changes than Intel’s PTT), and you get a prompt for TPM confirmation after updates like KB5077181.
You Get What You Pay For
That’s not to say ASRock is bad. For enthusiasts and DIY builders, their boards offer decent value and performance. But when it comes to firmware maturity and seamless integration with Windows security features, they’re noticeably behind the big OEMs.
The takeaway? Platform matters. As Windows continues to evolve its security posture, particularly around Secure Boot, TPM, and boot checks, users should expect some variation in how different systems respond to updates. OEM systems generally offer a smoother ride. DIY builds like my ASRock-based Flo6, appear to need more attention and manual intervention.
For those who live in the trenches of Windows-World, it’s just another reminder of how things sometimes work, or not. The best antidote is to know your hardware, expect the unexpected, and keep recovery media handy, just in case something goes awry. I’m glad I didn’t need recovery for this update. Indeed, I started wondering when I had to cycle power for a cold start, and an extra reboot to get to the desktop.