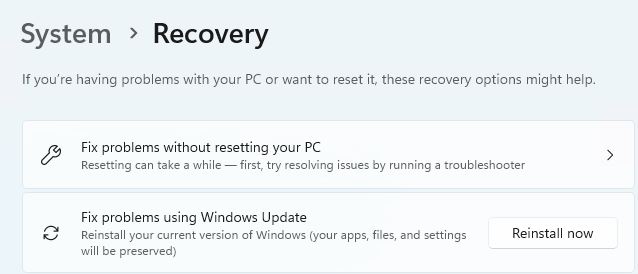
I guess it’s been a long time coming, because MS has waltzed around this topic for two years or more. The latest top-level Insider Preview now includes the option shown in the lead-in graphic. That’s right: Canary Build 25905 gains upgrade repair install capability via WU, built-in. This may make it unnecessary to visit UUPDump to generate ISOs which may then be mounted for such use.
What Canary Build 25905 Gains Upgrade Repair Install Means
Visit Start → Settings → System → Recovery, then look for the item labeled “Fix problems using Windows Update” (as shown in the lead-in graphic). This takes you through a number of screens en route, as shown here:
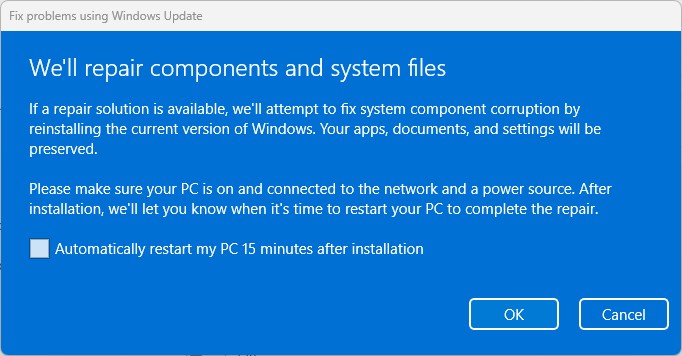
First you must grant permission for the repair to start
After you click OK (irrespective of whether or not you allow a timed reboot), you’ll move into Windows Update where you’ll see a display like this one: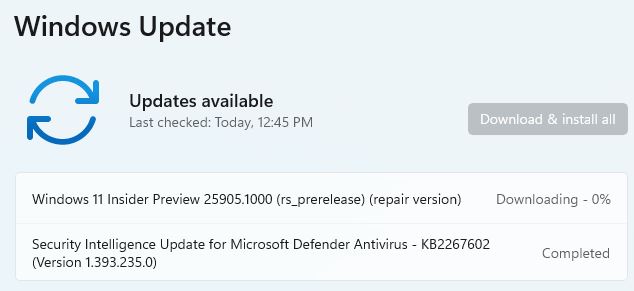
Windows downloads and installs a repair version of your OS, before moving into the post-GUI phase.
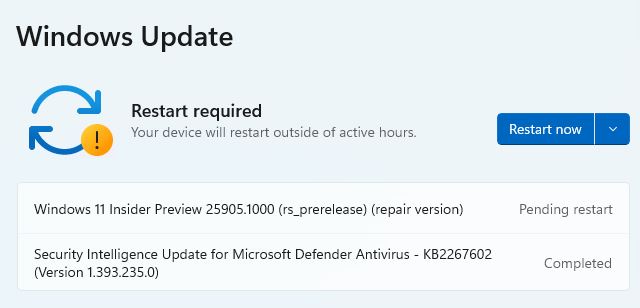
This can take a while: on my 2018 vintage Lenovo ThinkPad X380 Yoga, it took an astonishingly long 45 minutes to download and install to the first reboot. I was able to keep working until then, but after that, the installer took the desktop away for about another 10 minutes. When it’s time to reboot to continue the repair install you’ll see something like this:
Once the GUI installer gets done, you will restart to complete repairs.
After the restart warning, it takes another 3 minutes to get to the actual reboot. Then the real post-GUI work begins. All in all it took 55 minutes to get to a desktop as the repair install completed: 45 minutes for download and initial install; 10 more minutes for reboot and post-GUI install.
Trade-offs, Trade-offs
Here’s the deal: it takes about 12 minutes on the same PC to use a mounted ISO to get through the same process. But that means building a current ISO from UUPDump which takes about 25 minutes to complete. Thus it’s a matter of more personal effort to do it manually via UUPDump (37 minutes) for a little less time versus the ease and convenience of letting WU handle it for (but taking 55 minutes to complete). Interesting!