The electrician visited our house early today to fix some switches. He also helped us find a GFI plug we didn’t know we had (duh!). He had to turn off power at the breaker box momentarily, so all the PCs went down. I took that opportunity to pop the case on the new Ryzen 5800X build. I moved the NVMe SSD from the M.2.2 slot to the M.2.1 slot. That’s when I learned this new NVMe system delivers formidable punch power, I/O-wise. Let me explain.
If New NVMe System Delivers Formidable Punch, How So?
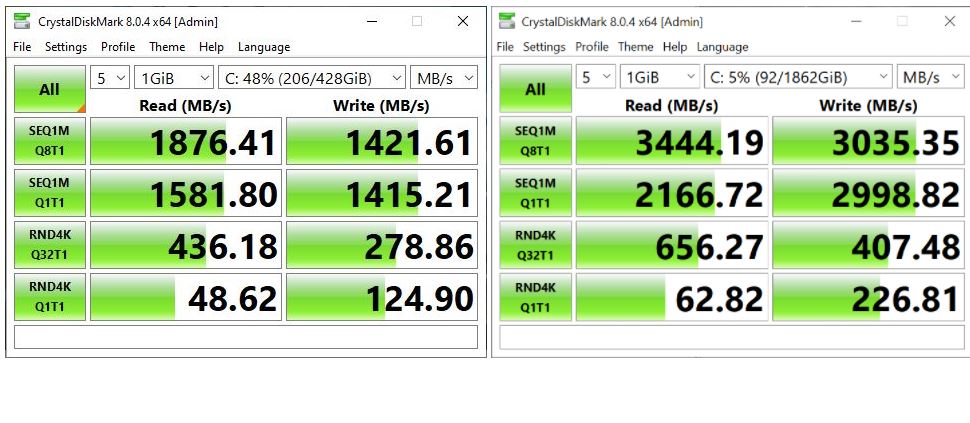
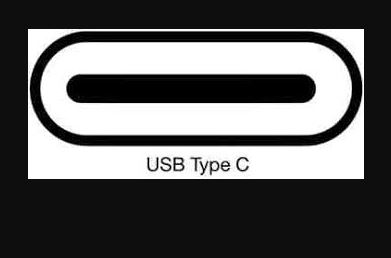
We’re talking about the transition from PCIe x3 to x4, along with a new generation of SSD controller technology here. The lead graphic shows CrystalDiskMark 8.0.4 results from my 2016 vintage i7-6700 system left and the 2021 vintage Ryzen 5800X system right. The underlying NVMe drives are Samsung 950 PRO 512GB left, and Sabrent Rocket Q 2TB right. The speed increase ranges from 1876.41 vs. 3444.19 (upper left), or 1.83x, to 124.9 vs. 226.81 (lower right), or 1.75x. The biggest differences occur in the upper right cell, and the one beneath it. Those ratios are 2.13 and 2.12, respectively.
Thus we’re talking about a speed boost ratio for I/O in the neighborhood of 7/4 at the slowest and 15/7 at the fastest. In roundish numbers, say 2:1. That’s pretty decent. I daresay it’s a big enough difference to be noticeable. I can tell the difference in ways that range from working with the filesystem, to performing backups, to running applications, and more.
Where Value Sits…
I’m still learning how the new system works, and what it can really do. I just ran WhyNotWin11 on the PC and it doesn’t have TPM turned on. I just checked the Asrock website. Happily it provides instructions on how to turn on fTPM in BIOS for that motherboard. It’s a single, simple option, so I’ll take care of it the next time I reboot. Then, the system should be ready for Windows 11.
Switching the NVMe from the M.2.2 slot to the M.2.1 slot delivered the promised speed increase. It also made the 2 previously blocked SATA devices on that machine visible. So far, it’s been a peach to work with. The speed and capabilities of this current-gen Ryzen processor definitely impress. I am indeed inclined to think the upgrade was worth the cost. I’m still waiting for Nvidia 3070 cards to come down in price before endowing that PC with more graphics oomph, though.
Stay tuned. I’ll report in on system temps and stuff, and take a few pics of the build later this week. Should be fun!