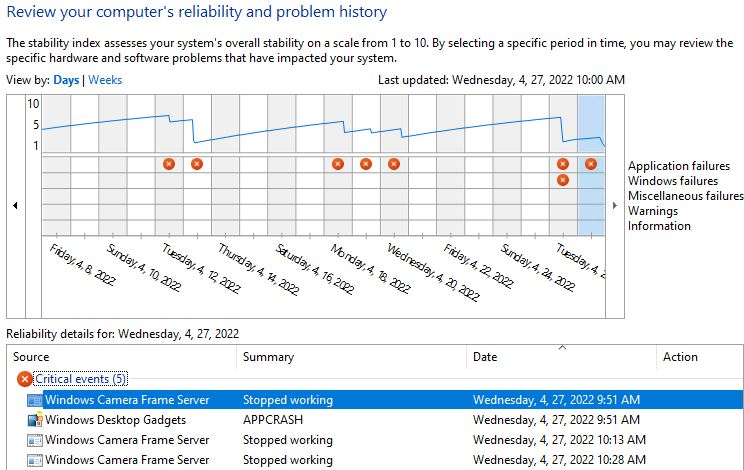
What on earth does this article title mean? Glad you asked! KIR stands for Known Issue Rollback. Once a Windows 11 PC gets the cited KB installed, it may not run properly if booted into Safe Mode (no networking). MS suggests in its Known Issues discussion that users boot into Safe Mode with Networking. This avoids looping Explorer crashes that otherwise cause screen flickering. Hopefully, the title now makes sense. KB5012643 Safe Mode bug gets KIR means MS will automatically apply a rollback of the offending feature to PCs that tag WU servers. A reboot is required for the fix to do its thing.
When KB5012643 Safe Mode Bug Gets KIR, What Happens?
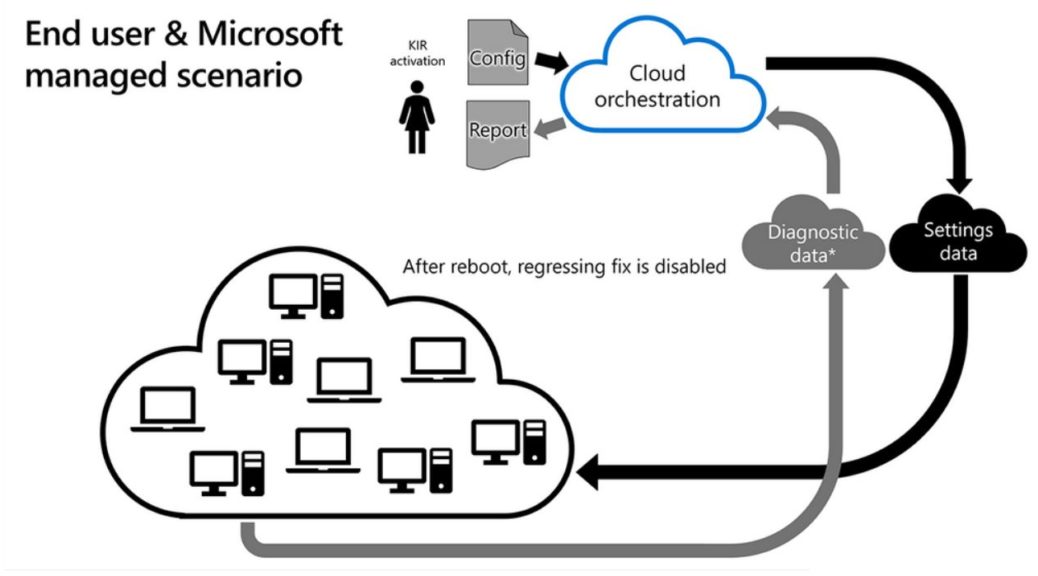
You can learn more about Known Issue Rollback in a Windows IT Pro Blog post from March 2021. It’s entitled “Known Issue Rollback: Helping you keep Windows devices protected and productive.” Here’s what this item states. KIR “… is an important Windows servicing improvement to support non-security bug fixes, enabling us to quickly revert a single, targeted fix to a previously released behavior if a critical regression is discovered.” In simpler terms, MS can tell WU to back out individual update package components.
Behind the scenes, policy settings either enable or disable code paths for “before” or “after” versions of code. If the “after” version is enabled, the update applies; if the “before” version is enabled, it reverts to the previous version.
Here’s how it works, quoted from the afore-linked post:
When Microsoft decides to rollback a bug fix in an update because of a known issue, we make a configuration change in the cloud. Devices connected to Windows Update or Windows Update for Business are notified of this change and it takes effect with the next reboot.
This is depicted in the lead-in graphic for this story.
Read the Post for More Deets…
There’s lots of great discussion in the Known Issue Rollback blog post. If you remain curious about its workings and capabilities, check it out. There’s also a much more technical exploration of KIRs from annoopcnair.com available for those who really want to get into the weeds. It covers details about managing and filtering group policies, and working with the KIR Policy Definitions Setup Wizard. I didn’t know you could do that, so that makes this good stuff!