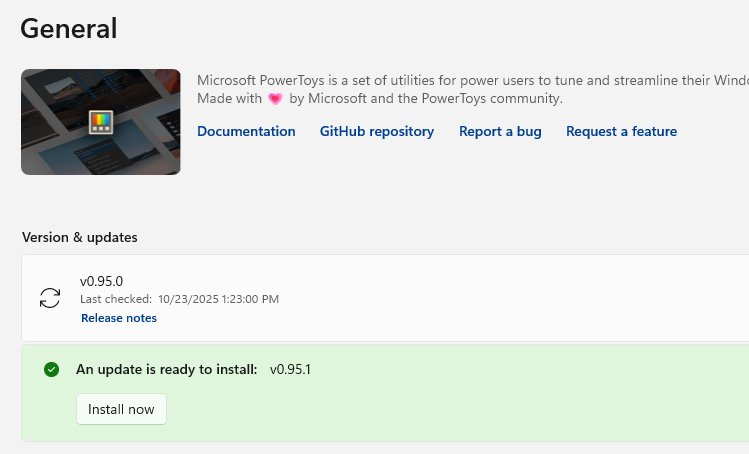
Just over a week ago, the PowerToys dev team dropped v.0.95.0. Highly touted amidst its new features: a Light Switch toy, which defines the default key combo Winkey-Ctrl-Shift-D to toggle Windows desktops from light to dark mode, or vice-versa. It’s also turned on by default. As I couldn’t help but notice after that, my PC(s) started toggling between light and dark mode with no help from me. Yesterday, the team dropped a new version: 0.95.1. It’s really worth installing because in that release, PowerToys fixes random Light Switch toggle behavior. I’m glad!
Why PowerToys Fixes Random Light Switch Toggle
PowerToys are supposed to work according to the user’s direction, not on their own recognizance. It’s a little disconcerting to be plugging away on one’s desktop and have the mode change whenever it feels like it. The timing was interesting, too: sometimes, it might happen once or twice a day. Sometimes, it would switch back and forth every 30 to 90 seconds. Disconcerting!
It’s easy enough to switch back if this happens to you. Fortunately, the key combo is quick: it’s close together and easy to enter. But better to avoid spontaneous mode switching if at all possible. That’s why I’m delighted to see an update that addresses such behavior sooner rather than later.
What the Release Notes Say…
The first Highlights entry is ALL about Light Switch. It lists 6 different fixes including: turning off enabled by default, not allowing sunset calculations to over-ride Manual time schedule, and renaming “Manual” to “Fixed Hours” mode. There’s even a new off mode that disables the switchover schedule but keeps the key combo working. Here is the new control pane for Light Switch:
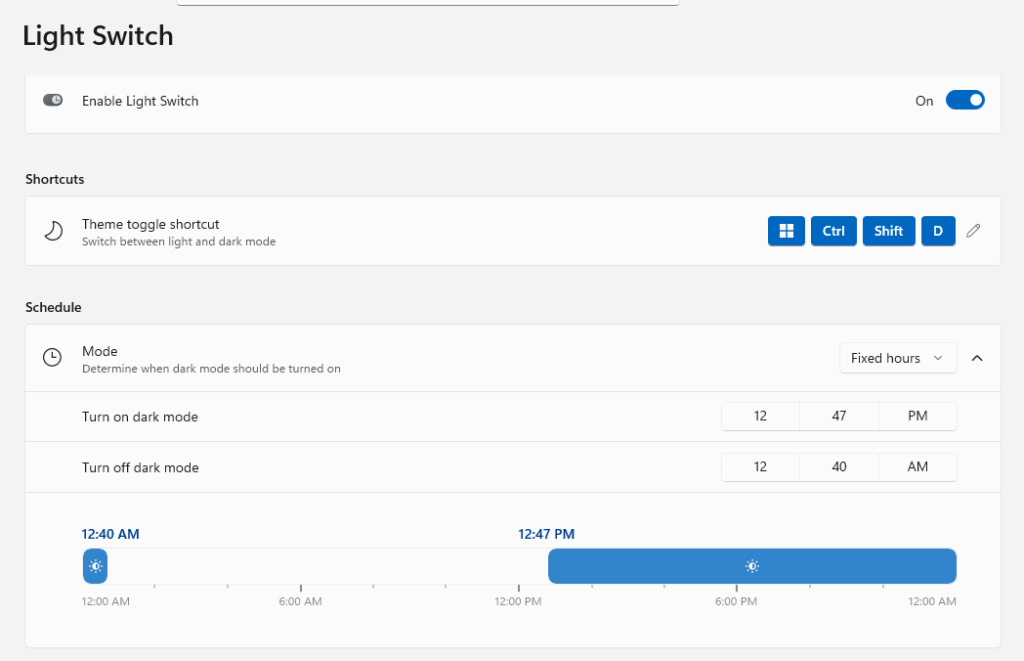 I’ve already turned scheduling off because I don’t switch modes by time of day. If you use PowerToys you’ll want to update to v0.95.1. I’m glad to see this fix so soon, because it was a little disturbing.
I’ve already turned scheduling off because I don’t switch modes by time of day. If you use PowerToys you’ll want to update to v0.95.1. I’m glad to see this fix so soon, because it was a little disturbing.
But hey! “A little disturbing” describes a pretty familiar feeling — for me, at least — here in Windows-World. How ’bout you?