Last Friday, we picked son Gregory up at the airport: he’s home for the holidays from college. That evening, he mentioned his laptop — a 2019 vintage Lenovo ThinkPad X390 Yoga — was “stuck on updates.” Boy, was he ever right: i found myself fixing Windows 11 boot loop as the machine hung after the post-GUI reboot in attempting to get through the 23H2 feature upgrade. Stuck, stuck, stuck indeed.
Fixing Windows 11 Boot Loop Takes Thought & Recall
As soon as I turned the PC on, I could tell it was cycling on processing updates. It just couldn’t seem to get past the spinning circle stage after the initial reboot. Multiple tries later — 3 of them, to be exact — the Windows bootstrap facility presented me with the recovery menu. “Aha!” I though “now I’m getting somewhere…”
Of course, then I had to remember to turn off secure boot in the UEFI so I could actually transfer control to a bootable WinRE environment on a flash drive (UFD). Startup repairs didn’t do it. The Macrium Reflect Rescue Media’s “fix boot problems” didn’t do it, either. But when I stuck the DaRT (Diagnostics and Recovery Toolset) UFD into the machine it finally got through a boot-up to alternate media.
On the next reboot, Windows recognized it was stuck in the middle of a failed update. It then commenced rollback to the previous 11 version and reached the desktop. At that point, I was able to run another Reflect backup (I did), and then start rolling forward again.
All’s Well That Ends Well
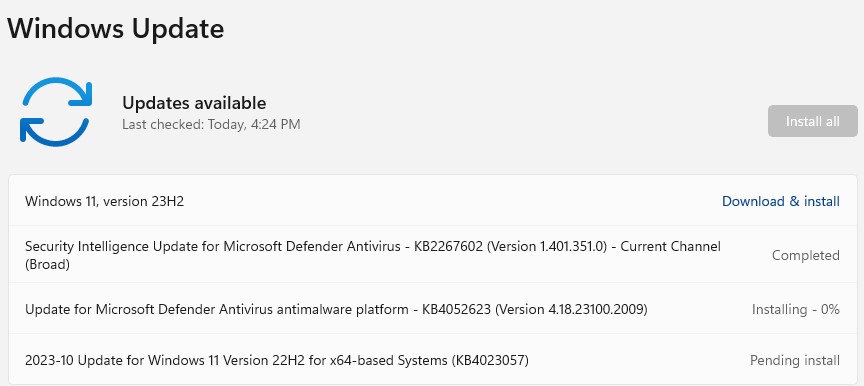
The pending Cumulative Update completed successfully, and rebooted correctly. I then fired off the 23H2 upgrade and crossed my fingers. This time, it completed without a hitch. The X390 is now fully caught up, cleaned up and has been backed up one more time.
I’m not sure what caused the first 23H2 attempt to hang in a boot loop, but it didn’t fall prey to that again. I think it may have been the attempt to apply the CU, then the 23H2 upgrade, in a single go. This time around, I made sure to reboot after the CU, before attempting the 23H2 upgrade. By the time I worked through all the steps, the whole shebang took about 2 hours to fix. We were all glad when it was done — me, especially.