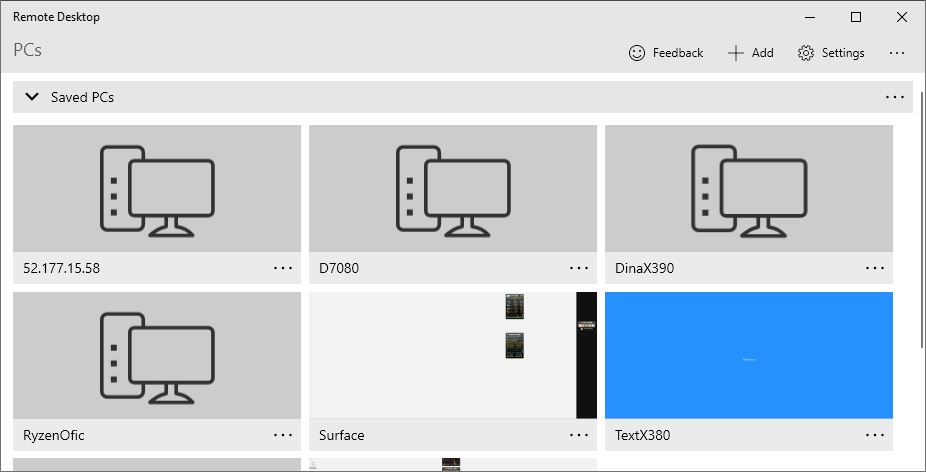
Here’s an interesting problem that I apparently share with lots of people. Try searching on “can’t login to RDP” or “MSA login to RDP doesn’t work.” You’ll see what I mean. For me, MSA login doesn’t connect via RDP from my trusty Win10 production desktop to my new Ryzen 5800X build. Sigh.
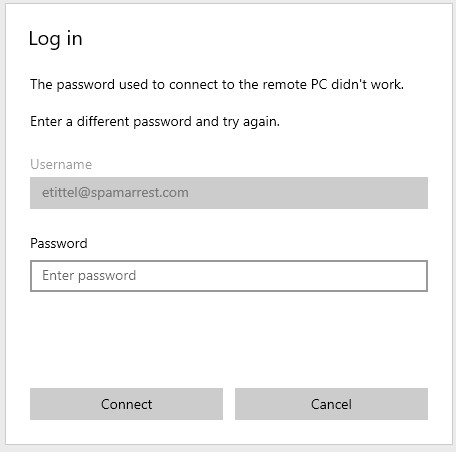
So, of course I went through all kinds of contortions and research to try to get it working. I tried a variety of GPO settings, registry hacks and more, all without getting any love. I spent 45 minutes trying to make this work to no avail. Even though I double-checked my passwords (and in one case, reset it just to make darn sure) I kept getting errors. Either “The password used to connect to the remote PC didn’t work” or “The credentials didn’t work” (RDP app and mstsc.exe, respectively).
Words alone can’t convey the frustration in using a known, good, working password and getting such an error. Ouch!
When MSA Login Doesn’t Connect Via RDP, Use Local Account
Then, in several of the posts I read online, I noticed that similarly afflicted individuals succeeded in opening an RDP session using a local (client) account. So I set up a local account on the client PC using the “Add account” facility in Settings → Accounts → Other Users. Hint: you have to say you don’t know the user’s sign-in info to get to the right screen, where you choose the “Add a user without a Microsoft account” (MSA) to create a local account. Sigh again.
So, I created an account named LocalU, and then promoted it to Administrator status. Then, on my next RDP attempt into that PC the login succeeded using that account name and its associated password.
Even though you can’t always make Windows do exactly what you want, you can often find a way to get what you need through some workaround. This is actually a pretty good example. I can’t say I’m happy about this (and plan to report it to Feedback Hub next). But at least I can RDP into my new desktop. This will be very important when I start migrating files and stuff from the current production desktop to what will be my new production desktop next month.
Stay tuned! I’ll keep you posted as things progress in their usual “two steps forward, one step back” fashion. Should be fun…