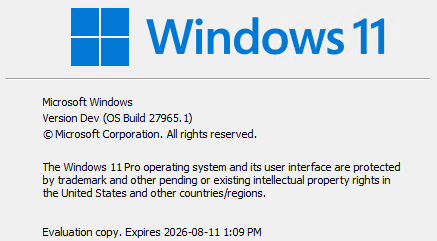
On the last day of September, the Windows Experience blog announced “the availability of the Windows 11 2025 Update (aka Windows 11, version 25H2).” A little careful perusal of this info, and some checking from your humble author shows that availability not only includes production versions. It also includes Insider Preview versions in the Release Preview and Beta Channels as well. By extension that means Dev and Canary Channel fall outside this umbrella. That’s what I mean when I say “Version Dev Gets No 25H2,” as you can see in the lead in-graphic (shows an ambiguous “Version Dev” instead).
Version Dev Gets No 25H2 Means More Than It Says
On my Canary test PC (the stalwart, still kicking 2020 vintage Lenovo ThinkPad X12 Hybrid Tablet) the version line from winver.exe gives things away. It reads “Version Dev” instead of 24H2 or 25H2. Both Dev and Canary Channels fall outside the Windows 11 versions that can upgrade to 25H2 at present. That’s because they belong to a different Windows 11 Build branch, with higher build numbers that bypass 25H2 entirely. That’s probably why MS forgoes 24H2/25H2 nomenclature in identifying the version as shown in the lead-in screencap.
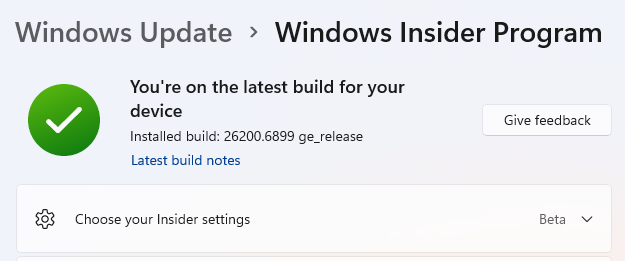
OTOH, I was able to use the Installation Assistant yesterday to upgrade my Beta Channel test PC to 25H2. It shows the latest build status in Settings > Windows Update > Windows Insider Program, as you can see here
 But it also shows up as 25H2 in Winver, and up-to-date in WU, as you can see here:
But it also shows up as 25H2 in Winver, and up-to-date in WU, as you can see here: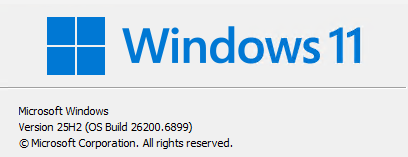 It’s all a matter of how close the bits come to matching the currrent production version of Windows 11. Because Canary and Dev Channels are further out, they’re not able to show a 25H2 base. That’s by design.
It’s all a matter of how close the bits come to matching the currrent production version of Windows 11. Because Canary and Dev Channels are further out, they’re not able to show a 25H2 base. That’s by design.
Interesting that Beta and Insider Preview Channels can move on up to 25H2 though, while Canary and Dev remain in the 24H2 zone. This will be interesting to watch in the months to come. I wonder if Canary will get its own version, or stay lumped in with Dev? We’ll see!