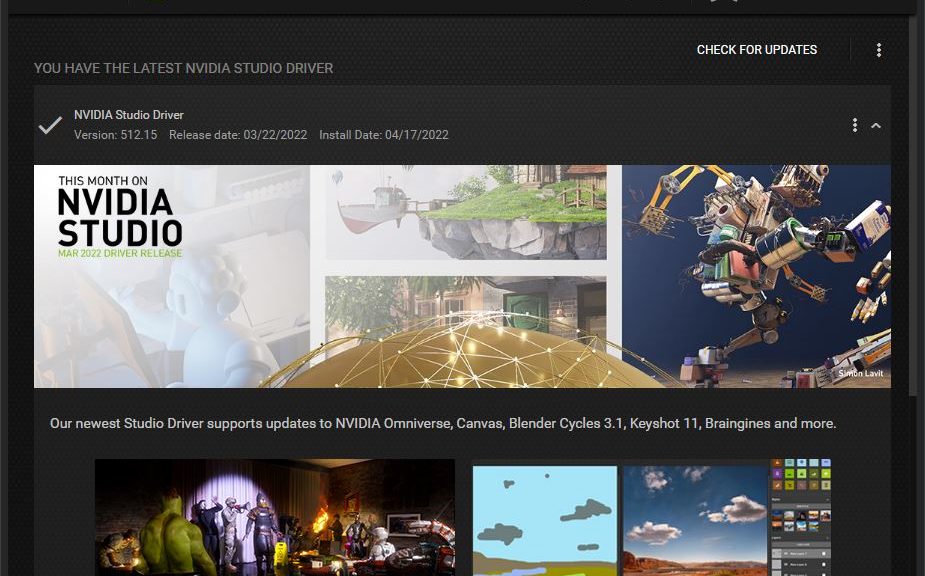
Yesterday, my production PC (Windows 10, i7-6700, 32GB RAM, 3070 Ti GPU) started the “blinking thing” again. As soon as I logged in, the right-hand monitor would go black then come back at irregular intervals. Previous episodes have responded to a driver update. But this time, no such update was handy. But my 3070 Ti runs either a gaming (for game play and high frame rates) or studio (for creative and production work) version. This time, fixing the blinking monitor required Nvidia Studio Driver to do its thing.
Why Is It That Blinking Monitor Requires Nvidia Studio Driver?
This issue has been popping up on my production PC since I switched out the 1070 Ti for the oversized 3070 Ti in January. I’m starting to wonder if my power supply may be having issues with the load on this system.
Reliability monitor doesn’t show any errors. But a dive into Event Viewer shows a Service Control Error 7031 that points to the Nvidia Local System Container at around the times I was getting the blink behavior. Since I’ve switched from the Gaming version of the driver to its Studio counterpart, the error has not resurfaced. Looks like it may be some kind of software glitch after all.
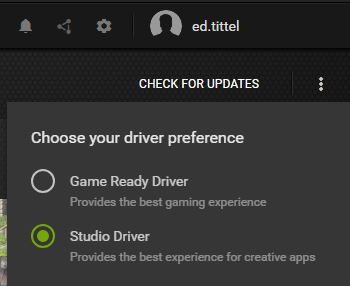
GeForce Experience lets you switch between the two driver flavors pretty easily. Simply click the vertical ellipsis to the right of the Check for Updates item and it gives you a radio button to pick one or the other, like so:
Fortunately for me, switching from”Game Ready” to “Studio” restored my system to proper operation. Good thing I’m not a serious gamer, eh?