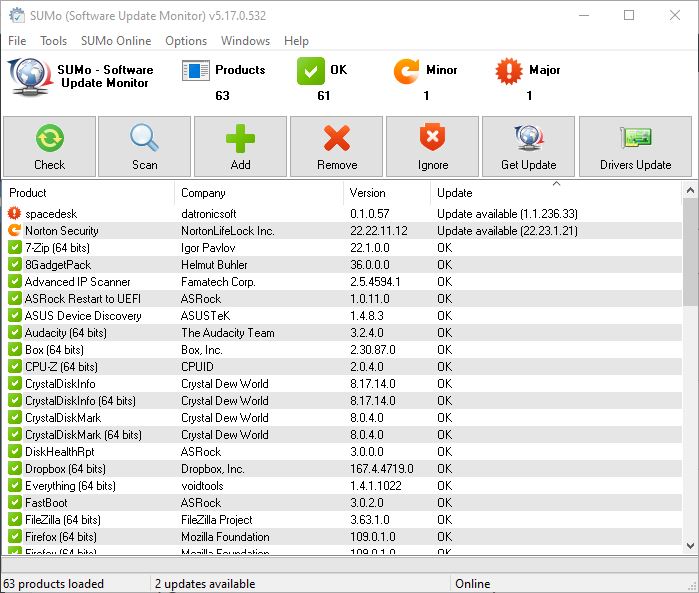
Oh boy! For more than a few minutes yesterday, I thought I’d completely lost my now-ancient Surface Pro 3 hybrid tablet. It took me a while to diagnose, but it was actually a Surface Pro 3 dock fail, not the PC itself. Seems that the brick that provides power to the dock is no longer working. It wasn’t charging the battery anymore, so once the battery died, so did the PC.
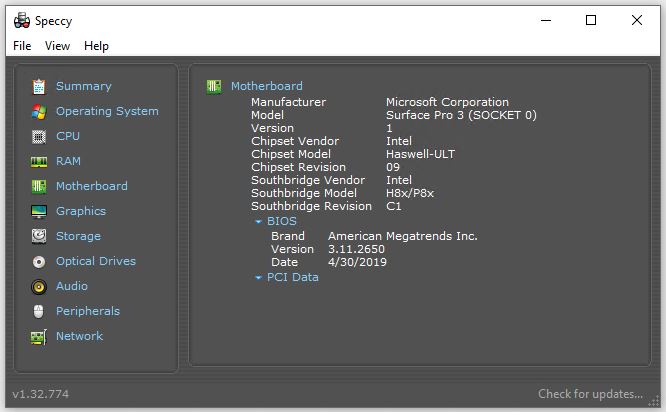
As you can see in the Speccy motherboard info screencap above, this unit goes all the way back to the Haswell CPU days. That makes it a Gen 4 Intel CPU. According to Intel, this model launched in Q3 2013, about 9.5 years back. That’s a long run for any PC, if you ask me.
After a couple of tests, I determined that power to the dock itself wasn’t working.
Diagnosing Pro 3 Dock Fail
At first I couldn’t get the SP3 to keep running. It would start up, then immediately fall over. I checked the battery and saw it had 0% charge. Upon leaving it alone and plugged into the dock for a couple of minutes, the charge level remained the same. “Aha!” I thought “No power to the charger, no power in the battery.”
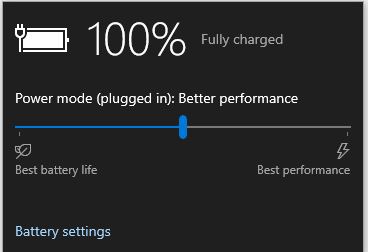
And so it proved to be. I still had the standalone charger for this unit. Upon plugging it into the wall and the SP3, the battery charge level started to climb. It took almost 2 hours but it eventually reached a full charge, to wit:
Given sufficient time, the SP3 returned to full charge.
Here’s the Question: Do I want to spend $41?
I can replace the AC adapter charger for the dock for the aforementioned price. Do I want to do that? I’ve been thinking about retiring this machine for more than year now. I’d been keeping it to ride Windows 10 to its retirement date with a machine likewise fated. But now I’m wondering if it’s worth it. $41 ain’t much, so maybe I will. Let me think on it, and I’ll post again…
Note added 20 mins later: I found a cheaper replacement on Amazon. For under $19 (including tax) I’ve ordered a new AC adapter for delivery next Monday. I’m hoping it will restore the dock to operation upon plug-in. I’ll follow up…
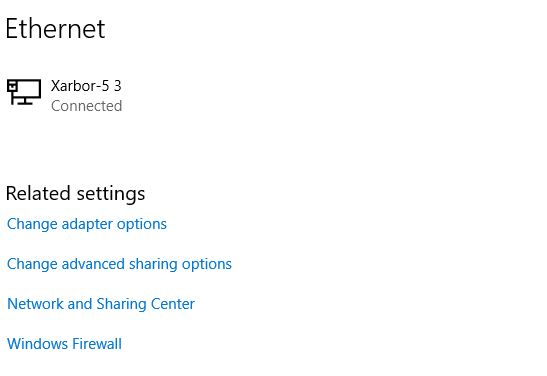
Note added Saturday AM, February 19: The El-Cheap AC adapter showed up at our front door late last evening (thanks Amazon Prime!). I removed the old unit and replaced it with the new one this morning. It works: as you can see in the next screencap the Surface has its wired GbE connection back, courtesy of the powered-up dock.
With power to the dock restored and Surface re-seated; Ethernet now works!
That was definitely worth the near-sawbuck expended for the replacement part!