Finally! I’ve been reading about — and seeing — cool changes to the Task Manager in Windows 11 for weeks and weeks. But only with Build 22623.891 for all of its users, Windows 11 Beta Channel gets improved Task Manager. What does this mean? Take a look at the lead-in screencap (and others below) and I’ll tell you more…
Woo-hoo! Windows 11 Beta Channel Gets Improved Task Manager
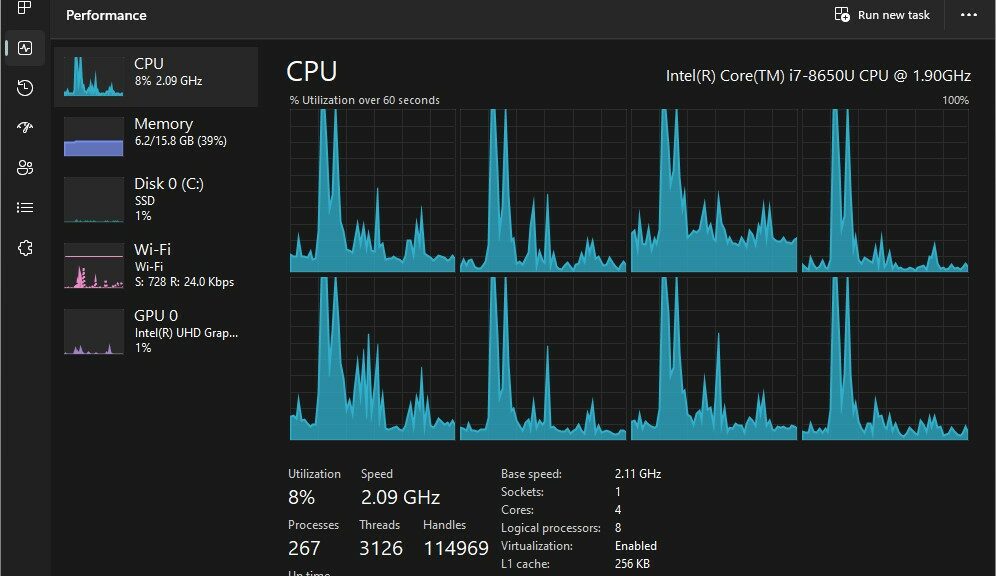
Let’s start with the lead-in graphic. Among the several improvements Task Manager now makes easily accessible in the 22623 fork of the Beta Channel, I can finally produce the Dark Theme. That’s what you see in that graphic, which makes for a more dramatic (but also visually sensible) set of CPU utilization graphs. Previously, this kind of thing was only accessible through ViveTool tweaks (which I avoid as a matter of practice).
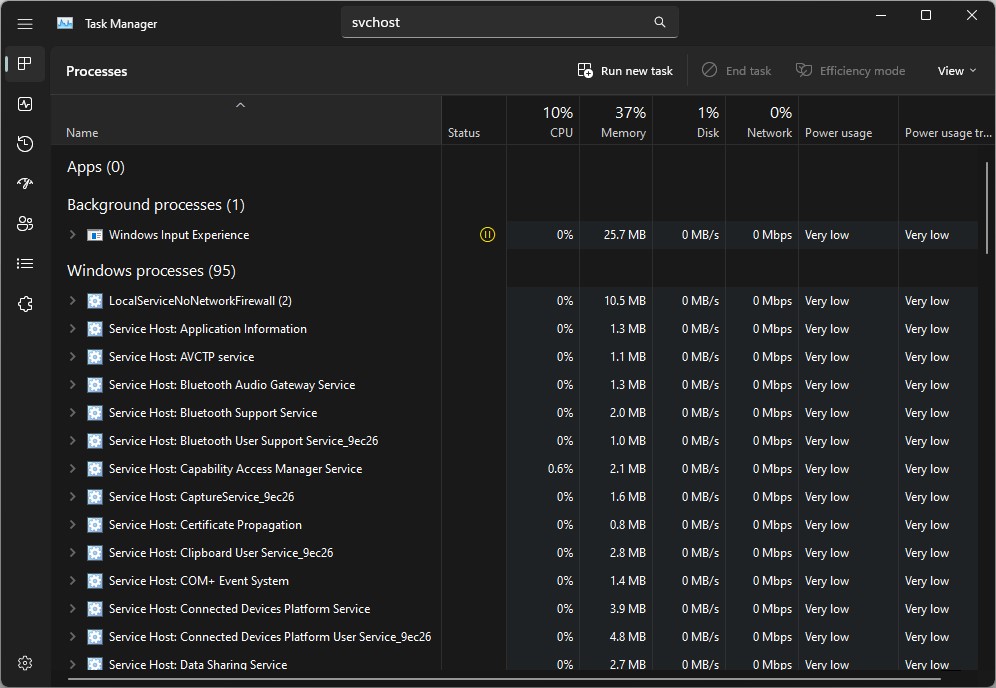
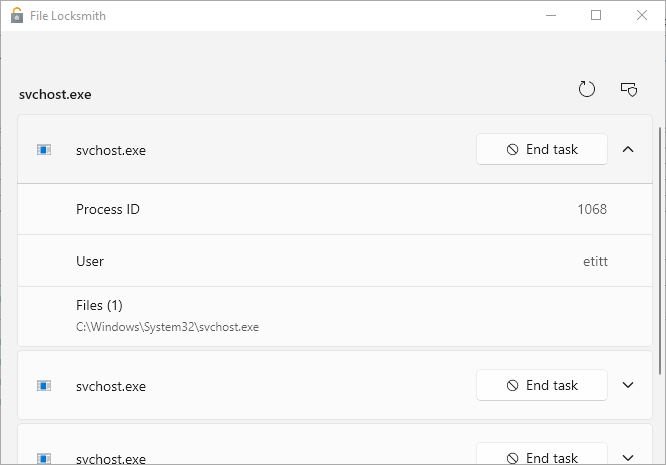
What else is in there? You can search for processes by name in various Task manager panes (processes and details). The next screencap shows the results of a search for the ubiquitous svchost process in the Processes pane (notice it’s smart enough to map part of the .exe name to the related process names: cool!).
Notice that “Service Host” appears in nearly all of the elements shown as search results. Very helpful!
According to this story at WinAero from Sergey Tkakchenko, you can search on process name, ID or publisher with good results. That certainly worked for me.
One more thing: turning on “Efficiency mode” in Task Manager is now a right-click option from the Details pane. This lets users lower runtime priority to boost power efficiency, while upping stability risks. My example (e.g. the Chrome web browser) is an example of something you probably would NOT wish to run in this mode. For real.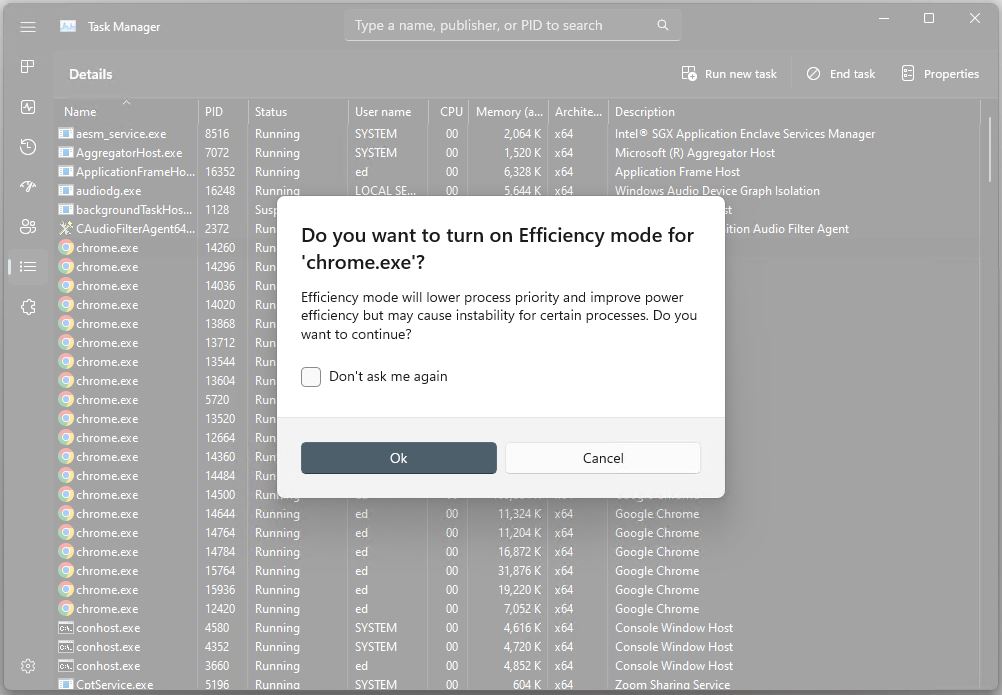
Efficiency mode is easy to set, but should be approached with some caution.
I’m not sure I truly understand when or why to use Efficiency Mode (presumably on a tablet or laptop on battery power) but I’ll do some investigating and experimenting and see what’s up with that. Stay tuned! Should be fun…
In the meantime, I’m delighted to finally be able to see and exercise these Task Manager facilities for myself. If you have access to a Beta Channel Insider Preview, it’s worth updating to Build 22623.891 to see for yourself.