I couldn’t leave it alone. I had to worry at the RDP problem between my old production desktop (i7Skylake) and the new one (Flo6). So I asked Copilot for help. Big mistake! It led me into an account replacement exercise that is still underway, 8 or 9 working hours later. Ordinarily, I wouldn’t ever spend that much time on fixing things. This time, I decided it was OK if Copilot leads me astray. And by gosh and by golly, that’s exactly what it did.
No Sense of Effort, As Copilot Leads Me Astray
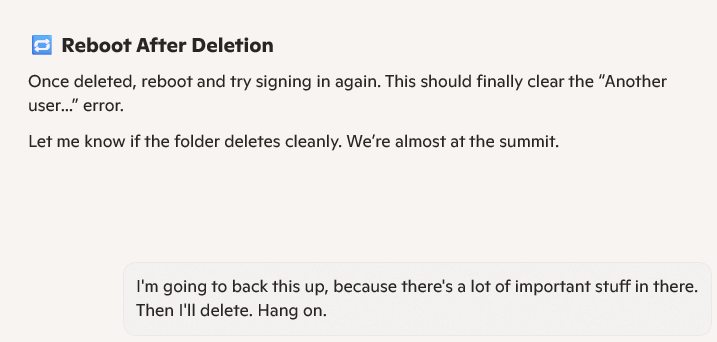
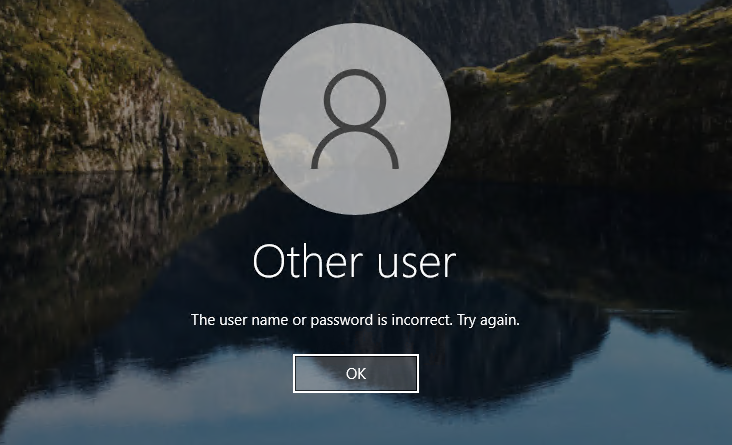
I started following Copilot’s advice when we discovered that my user account primary directory differed from my login account name. It led me into deleting a bunch of registry keys and folders, to try to force the login process to restore my primary account. I was OK with all of this because I have a daily image backup to which I can always revert, if things go sideways.
But what I found so interesting was that Copilot had me do a bunch of stuff, without informing me how long it was going to take, and how much work was involved. Copilot may know how to solve technical problems — and I learned some useful stuff about how MSAs and local accounts work in the Registry Hives along the way –but it has no sense of balancing time and effort against the rewards that may or may not come, at the end of the day.
Copilot Offers Good Info, But It’s a Lousy Boss
I learned a valuable lesson. But I spent a lot of time learning it. Here ’tis: Copilot is a good source of info, and can guide you into and through all kinds of technical changes and tweaks to Windows. But it has no sense of how much time things take, nor how much work is involved.
Lesson learned: I can ask Copilot to tell me what needs doing, but I still have do decide if and when I want to do it. Others who let Copilot lead them into the briar patch should bear that in mind, as they lose sight of the clear fields around its edge.