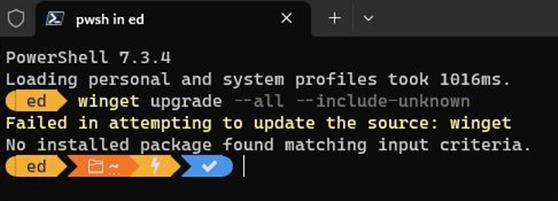
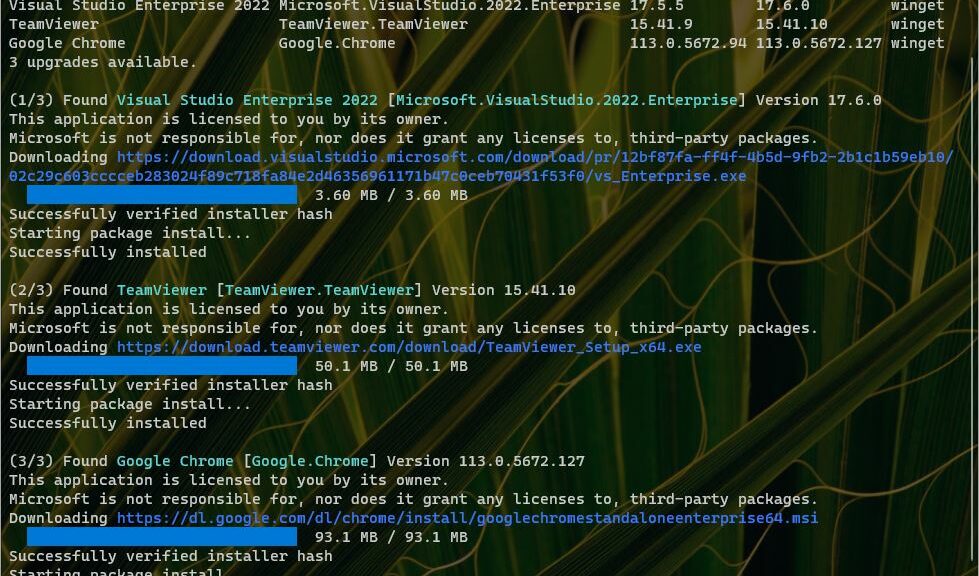
OK, then: yesterday dev lead Demetrius Nelson and his Winget team pushed an upgrade to winget. This comes courtesy of the Microsoft Store, and shows up as part of the App Installer and/or Windows Terminal packages. I noticed also that winget would occasionally throw the error “Failed in attempting to update the source: winget” as you can see in the lead-in screencap. What made it interesting was that it happens on some, but not all, of my Windows PCs. Now, let me explain why this post says that the “Winget upgrade may require cleanup.”
Why Say: Winget Upgrade May Require Cleanup?
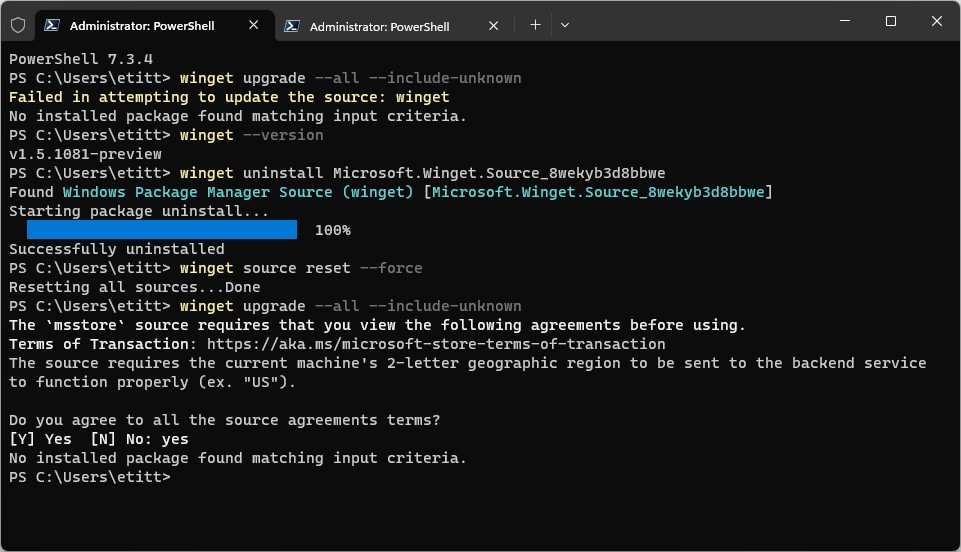
When I saw this pop up in the wake of the new release, I figured the changes involved in pushing it out the door might have been involved. So I contacted Mr. Nelson and sent him (among other info) the screencap that leads this piece off. He responded this morning and explained how I could fix the issue, using the commands:
winget uninstall Microsoft.Winget.Source_8wekyb3d8bbwe
winget source reset --force
The first string removes the winget package from the PC. The second resets the winget environment, which is why the user must agree to Terms again before winget will run. After that it shows no upgrades are available (“No installed package found matching input criteria” with no accompanying error message (“Failed in attempting to update the source: winget”).
Problem solved; case closed. It’s always good to get the fix right from the source. Had to laugh about the “It won’t break while the engineer is watching” comment he sent me, too. Isn’t that just the way things go in Windows-World (and elsewhere in life)? LOL
See the whole thing here:
The fix is in — and working! Good stuff…