With Dev and Beta Channel releases, it’s always “just a matter of time” before something gets wonky. Yesterday, in fact, I ran into difficulties upgrading one of my X380 Yoga laptops to Build 25227. In November 2021, I wrote a blog post here entitled WU Reset Tool Works on Windows 11. Good thing, because WU reset fixes weird Windows 11 upgrade freeze, too. Let me explain…
I’m Glad WU Reset Fixes Weird Windows 11 Upgrade Freeze
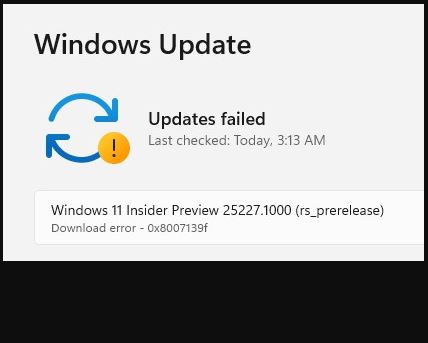
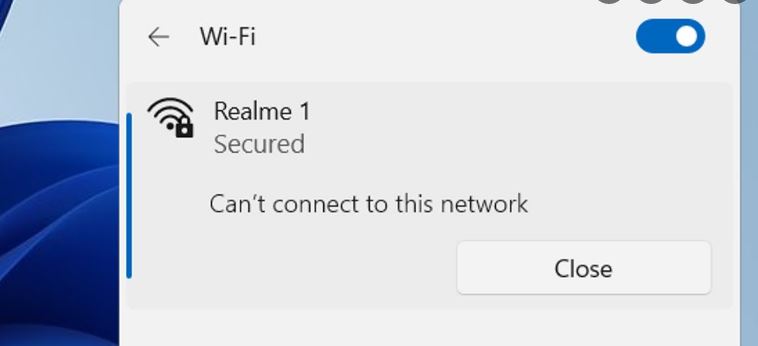
Here’s what’s weird about this failure. The laptop hung during the post-GUI update phase, after the old OS hands over control to the installer’s WindowsPE-based runtime environment. Indeed, it got all the way to 98% complete before it hung interminably.
Yet, as you can see, the hex code speaks to a “download error.” I have to guess there was some essential bit of data that the installer needed to read right at the end of the post-GUI installation process. When that failed, the whole shooting match went south. Stuck forever!
The Charm Came on the 2nd Try
I probably got lucky. I ran the invaluable reset/reregister batch file cited in the WU Reset Tutorial at ElevenForum, Then I tried the 25227 upgrade again: it worked this time! That said, this one took 30-40 minutes to complete (a fair while longer than previous but recent Dev Channel upgrades). But it sailed through to completion and is now working properly on the X380 laptop.
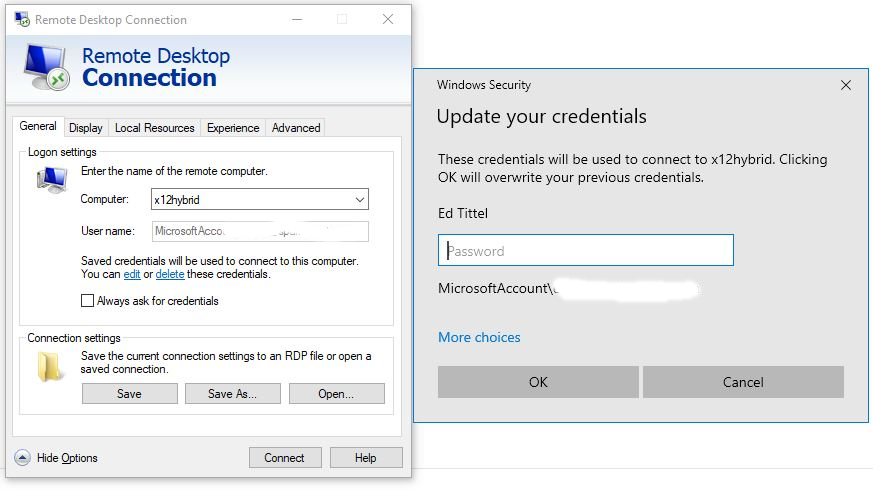
On the plus side, the login issues I’d been having with RDP on the same laptop also disappeared with the upgrade. That’s a relief. But on the minus side, my other Dev Channel test machine acted a bit wonky during the upgrade, too. It shut down after the reboot from the GUI phase into the post-GUI phase of the install. I had to manually power back on to finish the job. That hasn’t happened for a while with Dev Channel releases, either.
But hey! The purpose of Insider participation is to help catch — and hopefully kill — bugs and weirdnesses before they get into general release. We’re all just doing our jobs by finding and reporting this kind of stuff.
And that’s how it goes sometimes, here in Windows World. Good thing I enjoy it, and relish my appetite for problem solving and troubleshooting.