I must confess. I blew up a Lenovo review unit Wednesday trying to fix an update problem. Now after what I learned during that experience, I’m learning new backup post-blowup. First, I’ll explain the need for new backup; then the blowup,; and finally, the backup and recovery manuevers I must now make part of my review process. It all ends with an ironic footnote, as my precautions prove unneeded.
To begin with, I’d like to thank Amanda Heater and Michael Redd of the Lenovo Reviews team, based in North Carolina. They didn’t even laugh at me when I told them what I’d done. They simply offered to cross-ship me a replacement system while I returned the one I so thoroughly munged. Thanks, thanks, thanks.
Why I’m Learning New Backup, Post-Blowup
It all goes back to Paramount Software, maker of the excellent backup and recovery toolset known as Macrium Reflect. I’ve been a happy and satisfied use of same for seven years or more. But as of January 1, 2024 (now 18 months ago), the company dropped its free version of that software. In good conscience that meant when I updated my ComputerWorld story How to make a Windows 10 or 11 Backup, I had to recommend one or two free backup packages, as well as continuing my ongoing endorsement for Reflect (I own 8 licenses for version X and 4 for version 8, in fact).
So while I’m intaking the second iteration of a Lenovo ThinkPad T14s (the Snapdragon X variant of their thin-and-light 2-in-1 business laptop), I’m also learning how to install and use Easus ToDo Backup (one of the three free packages I mention in the February 2024 revision to the afore-cited CW story, the other two being AEOMEI Backupper Standard and MiniTool ShadowMaker Free).
It’s been both interesting and frustrating. I know Reflect so well now I don’t have to think about what I’m doing anymore: I just do it. In using Easus ToDo, I’m reminded of how idiosyncratic UI design can be, and how careful one must be in reading UI clues to understand how to define, schedule and run backups. Ditto for building and using recovery media. Long story short, I did figure things out, and I do have two backups of the T14s, working recovery media, and am ready to use them if needed. I’ve also saved a copy of the T14s BitLocker Recovery Key to a USB flash drive and my MSA.
What About That Blowup?
In working on the first of the two T14s laptops Lenovo sent me, I learned something about Windows 11 that I didn’t know, and would have preferred never to learn. In working through my normal intake process I ran Windows Update. It showed a pending CU that would not install, with the error code 0x8007000D, which indicates a corrupt Windows download or some issue with WU itself.
So naturally, I next ran the batch file from the Eleven Forum Tutorial: Reset Windows Update in Windows 11. This nearly always works to set WU back to rights, and let me get on with my updates. Not this time. The OS recommended, and my own experience concurred, that an in-place repair install was the next step in fixing this issue.
That’s where the blowup happened, as I encountered a Windows misbehavior I’ve never, ever seen before. I used the “Reinstall now” button in Settings > System > Recovery. It appears under the heading of “Fix problems using Windows Update.” It’s usually pretty foolproof and often turns a balky or misbehaving Windows OS into its tidy and proper counterpart. But first a short detour to describe the in-place repair upgrade or install.
More About the In-Place Repair Install
A repair install goes through two major phases. First, there’s a GUI-based portion, where it copies over the Windows OS installer and the files it needs to install the OS. Second, there’s a reboot after which a WinPE-based installer takes over and finishes building a new OS from a whole new set of files and data structures. Usually, Windows 11 reboots 2 or 3 times after the initial reboot as it finishes various aspects of that install process. When it’s done, a newly installed and presumably pristine version of Windows is running, usually devoid of the issues that prompted this repair fix.
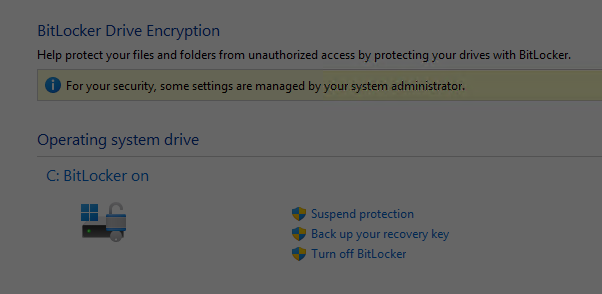
This time, on either the first or second post-GUI reboot, the boot handler brought up a BitLocker recovery key screen. It also informed me that something about the boot environment had changed enough during the install that this key was needed to proceed. Ooops!
What Makes BitLocker Key Request a Blowup?
I didn’t have the BitLocker recovery key for that machine locally, and it hadn’t yet propagated into my Microsoft Account (MSA) online. I literally couldn’t access the hard drive. When I attempted to use the Lenovo image recovery service, I couldn’t get it to fork over a digital download. I could buy a pre-loaded USB for US$29 but it could take as long a week to make it to my door. Lenovo suggested that I return the unusable T14s to them, while they would cross-ship a new, working one to me for next-day delivery.
That’s the machine I’m working on right now. And my first steps on that second iteration were to:
- Install Easus ToDo Backup, and make a full-drive C: image backup
- Build the ToDo Recovery Media (this bootable flash drive will let me restore any ToDo image even if the C: drive is inaccessible)
- Make a file copy of the BitLocker recovery key to that same bootable flash drive, should I need for any reason. I also forced a copy into my MSA online as well (I don’t always travel with a full set of UFDs).
This is a new and permanent set of intake activities when I get a new PC or review unit from an OEM like Lenovo (I’ve also reviewed PCs and laptops from ASUS, Acer, MSI, Dell, Panasonic, and HP in past years). If a repair install can provoke the Bitlocker key request, I have to be ready for that. Now, thanks to the foregoing steps, I will be.
Ironic WU Conclusion
The CU that caused me problems on the first machine also needed installing on the second one. It was KB5063060 (26100.4351 Out-of-band). It failed on the first attempt right after the machine came up for the first time upon unboxing. But this time, the Retry button resulted in a successful installation. The machine’s all caught up and I didn’t need to run the in-place upgrade repair install, nor to recover from its failure (and supply the Bitlocker key on demand).
I was ready for things to go south. I’m grateful they did not. But, as I can attest from painful recent experience, it’s better to have the recovery tools and data and not need them, than it is to need them and not have them.
And wow, it seems ever so appropriate to recite this saga on a day emblematic of mala fortuna: please note that it’s Friday the 13th. It can be a risky day in Windows-World, as in other worlds as well.