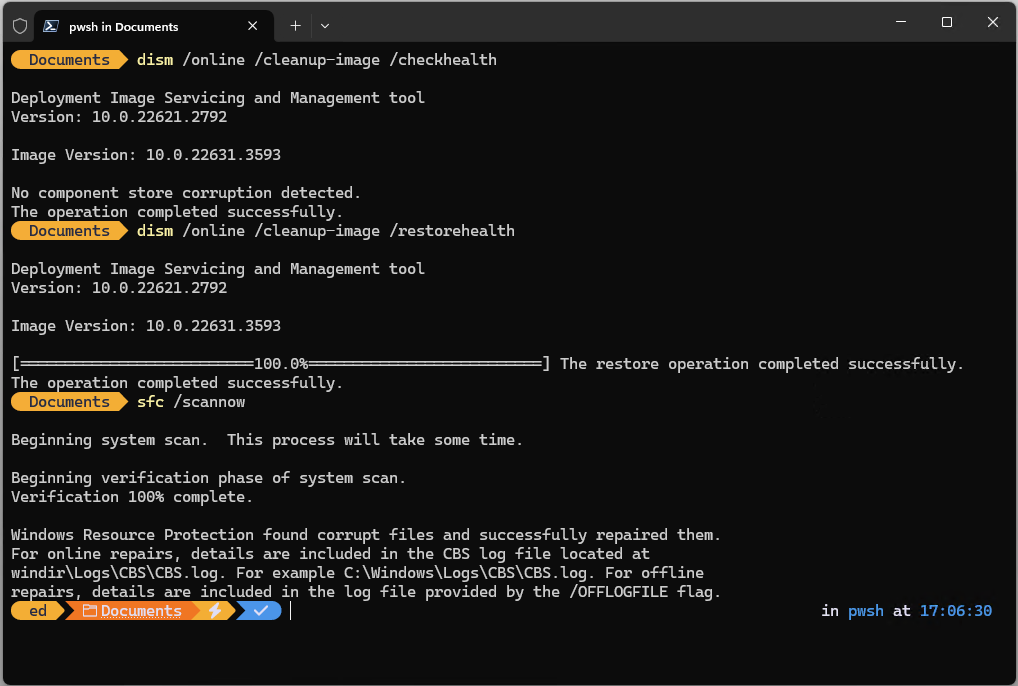
If I needed proof that “no good deed goes unpunished,” I got that yesterday. I was revising a story for Tom’s Hardware about fixing an IRQL BSOD. By way of example I ran a pair of DISM commands and the system file checker (shown at the end of this post). The second DISM command took a LONG time to complete and hung up at 62.3% complete. Then, when I jumped to another PC it did the same thing again. That’s why I’m digging into massive DISM delay this morning.
What Digging Into Massive DISM Delay Tells Me
A quick online search tells me I’m not alone. Indeed, there’s a Reddit thread entitled “DISM Restore health stuck on 62.3%.” It confirms what I’d observed on my own PC — namely, that the delay is NOT a hang, and the command will complete . . . eventually.
Next, I ran down the logs that get written when DISM /RestoreHealth is underway. First, I found a 10-minute gap between one timestamp and the next in the dism.log file. Then I used the same timestamp when that delay hit to look at CBS.log. Sure enough, the repair was mapping Windows Enterprise to the Professional Edition. This was followed by at least 3,371 files opened and examined (some lines open 1, others 2).
Based on a screen’s worth of entries summed and averaged it comes out to 3371 * 1.42 = ~4829 files in all. Obviously, that can take some time. The end of this activity explains what’s going on: “Repr: CBS Store Check completes.” Then a bunch of missing manifests or catalogs come in, with a large number of update downloads after that. Poof! 10 minutes is gone.
When DISM Gets Going, It’s Busy, Busy, Busy
So even though DISM /CheckHealth found nothing amiss, DISM /Restorehealth found itself with a lot of work to do. And that’s where the “missing 10 minutes” went. Seemed like forever, but it’s apparently a well-worn routine — if the Reddit post is any indication.
And boy howdy, isn’t that exactly how things sometimes go here in Windows-World? And I suppose I should be glad that all the current public Windows 11 release PCs experience the same thing. At least, it’s consistent . . .