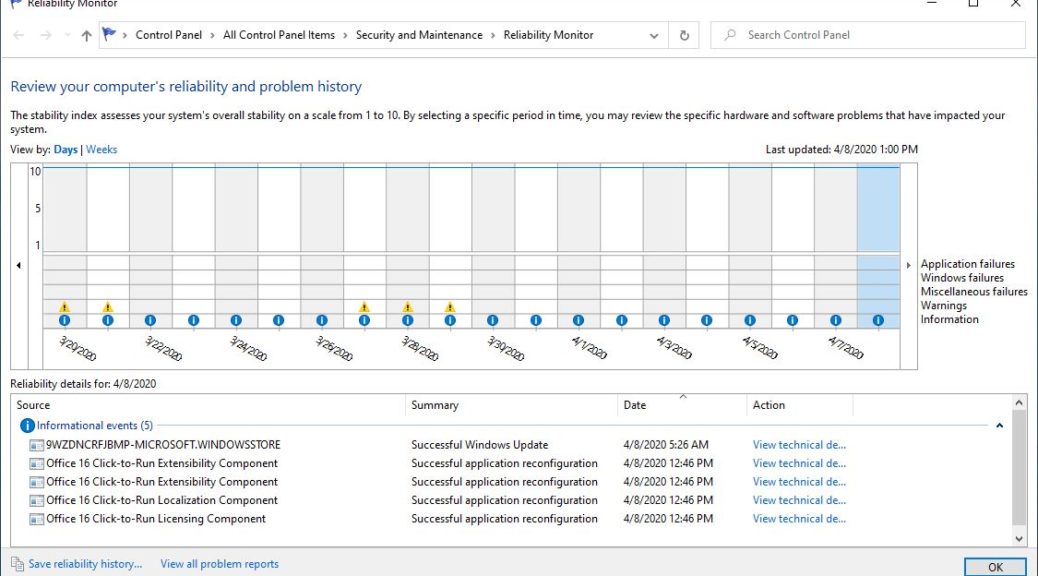
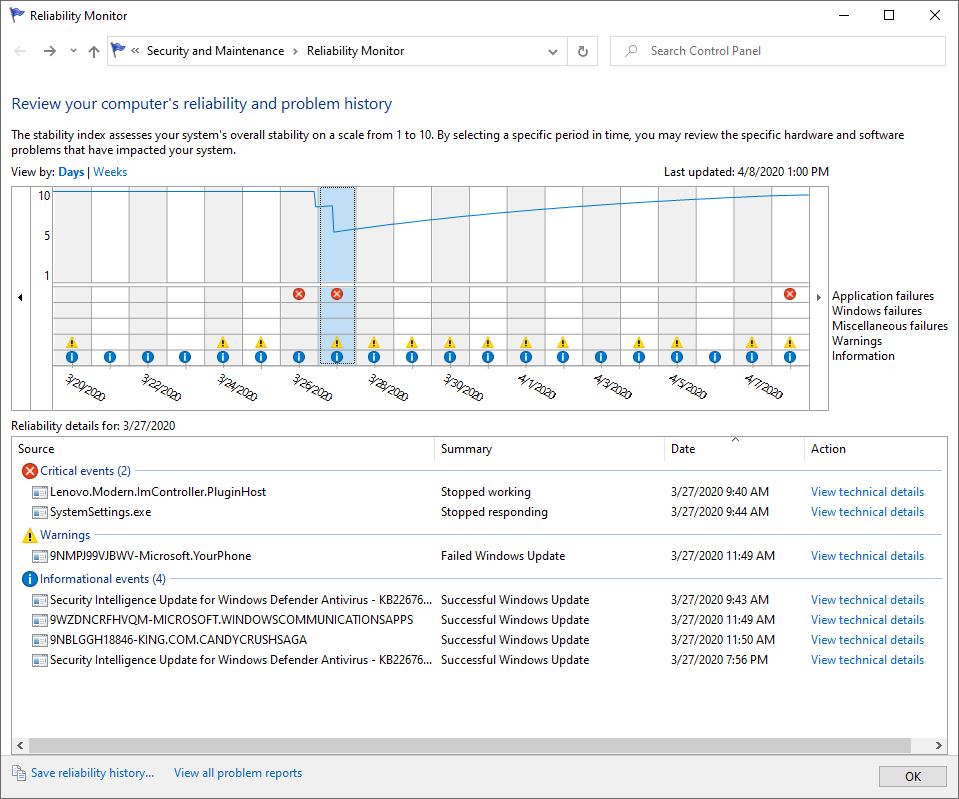
Here’s a blast from the past. In 1984, jarred spaghetti sauce maker Prego immortalized the phrase “It’s in there!” for its products. (Note: the link is to a YouTube copy of that very same TV advertisement.) But the tag line lives on, and comes with occasionally interesting applications. It helped me understand that Microsoft’s introduction of Pluton enacts Prego CPU philosophy.
What in Heck Does “Pluton Enacts Prego CPU Philosophy” Mean?
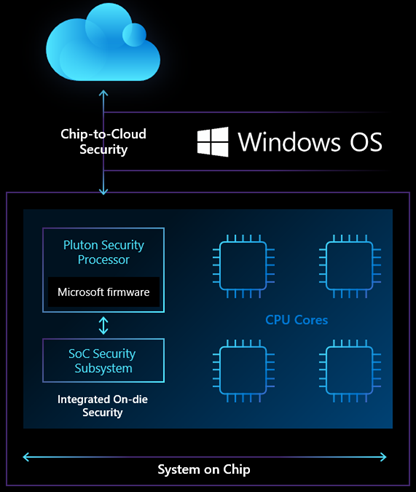
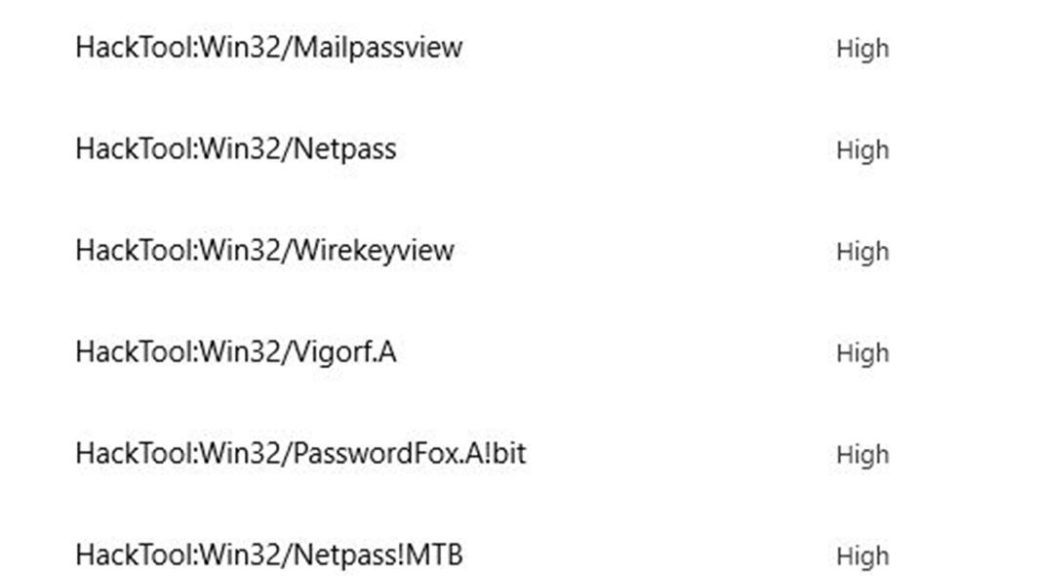
It means that functions currently associated with a separate chip called the “Trusted Platform Module” (aka TPM) move onboard the CPU die. That’s why I’m stuck on the Prego tag line “It’s in there!” It succinctly sums up what Pluton is and does.
On November 17, MS Director of Enterprise and OS Security David Weston wrote a post to the Microsoft Security blog. It explains Pluton nicely. The post is entitled “Meet the Microsoft Pluton processor — the security chip designed for the future of Windows PCs.” Therein, Weston reveals the notion of a ‘Pluton Processor’ as something of a misnomer — but a useful one. Here’s what he says to help explain Pluton, already “pioneered in Xbox and Azure Sphere.” (Note: I added the emphasis in blue bolded text):
Our vision for the future of Windows PCs is security at the very core, built into the CPU, where hardware and software are tightly integrated in a unified approach designed to eliminate entire vectors of attack. This revolutionary security processor design will make it significantly more difficult for attackers to hide beneath the operating system, and improve our ability to guard against physical attacks, prevent the theft of credential and encryption keys, and provide the ability to recover from software bugs.
Thus, Pluton is not really a processor per se. It’s a set of circuitry included on the die and tightly integrated into the CPU itself. This prevents attacks on communications lanes between a physically disjoint TPM chip and the CPU.
There’s a Scare Factor There
Apparently, recent research shows that the bus interface between TPM and CPU “provides the ability to share information between the main CPU and security processor…” At the same time, “…it also provides an opportunity for attackers to steal or modify information in-transit using a physical attack.” (Note: the preceding link takes readers to a Pulse Security research paper. It explains how sniffing attacks against a TPM permit BitLocker key extraction, used to read an encrypted drive.)
The Pulse Security paper describes ways to boost security to foil such an attack. But MS apparently took the work very seriously. In fact, it introduced Pluton to make communications lanes between CPU and a security processor impervious to attack.
Can Pluton Boost Windows PC Security?
Sure it can. It will indeed make sniffing attacks like those Pulse Security describes nearly impossible. And it should usher in a new, more secure approach to computing. This applies directly to handling “credentials, user identities, encryption keys, and personal data” (Weston’s words).
The real key, however, is that MS has all of Windows CPU makers on board with Pluton. That means AMD, Intel and Qualcomm . It will be interesting to see how long it takes for them to incorporate Pluton into their CPUs. We’ll wait awhile before the first Pluton-bearing chips hit the marketplace. I’m betting that Pluton will show up for both Windows Server and client OS chips as well (that’s not explicit in Weston’s post).
My best guess is that we’re probably two generations out. For all three makers of CPUs mentioned, it’s likely that their next-gen designs are too far along to incorporate the redesign and layout rework that incorporating a security facility on the die will require. That’s why it’s more likely two (or more) generations out, IMO. Stay tuned, and I’ll keep you posted.