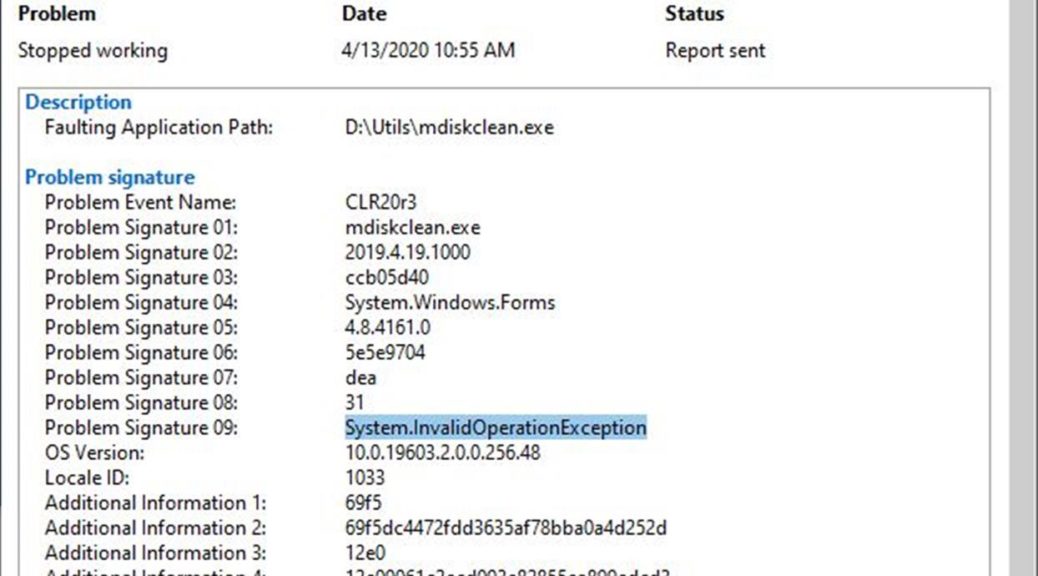
You know, there are more benefits to keeping software up-to-date than just avoiding security vulnerabilities. They even go beyond the pleasures of good housekeeping. When I couldn’t run Albacore’s excellent Disk Cleanup reaplacement (mdiskclean.exe) on my Lenovo X220 Tablet this morning, I started troubleshooting. Along the way, I found it ran just fine on my X380 Yoga (my other Fast Ring test machine). “Hmmm,” I said to myself, “let me compare the file dates.” And sure enough, I was running an April 2019 version of the project. However, the X380 was running a newer, May 2019 version. A quick online check confirmed that May 2019 is the latest and greatest version. Thus, I concluded that old MDiskClean.exe throws System.InvalidOperationException error. Those details appear in the lead-in graphic above.
If Old MDiskClean.exe Throws System.InvalidOperationException Error Then Update!
Indeed, my next move was to grab a copy of the current version. I replaced the old, outdated April 2019 version with the current May 2019 version. Then I ran the program again. This time, it worked like a charm. There was nary a trace in the Reliability Monitor of its passing, either. Sometimes, the easy fix is also the right fix. I’m glad to report that this is one of those times. The problem is solved.
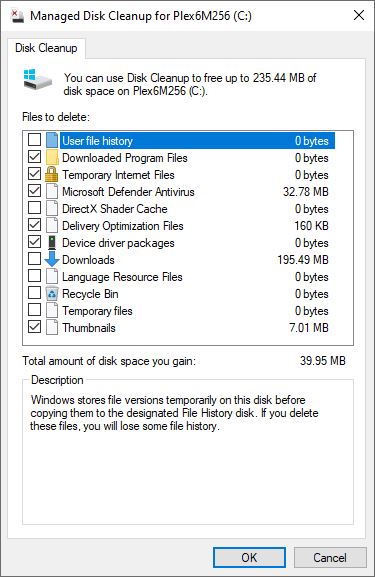
With the current (05.2019) version running and working, mdiskclean.exe looks exactly like Disk Cleanup, except it lets you show all available selections at the same time.
Disk Cleanup limits the display area to 5 items, so you have to scroll like mad to get through a big list.
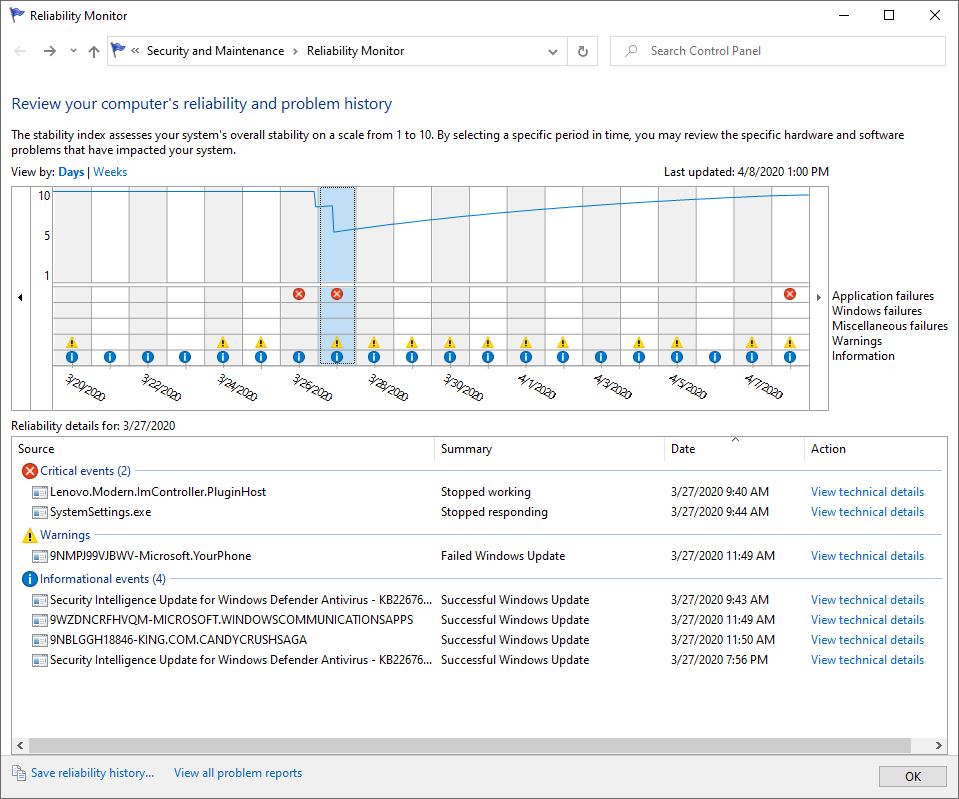
If you should run into application level errors in Reliability Monitor, it’s smart to check the application itself first before taking troubleshooting further. In this case, that was as far as I needed to go. Had that not helped, my next move would have been to run the system file checker (sfc /scannow) and to perform a DISM componentstore health check (dism /online /cleanup-image /checkhealth). Normally, that would be as far as one would need to go at the application level. Beyond that, though, comes an in-place upgrade repair install (TenForums Tutorial) and finally a clean (re)install (TenForums tutorial). Glad I didn’t have to break out any of that heavy artillery. Cheers!