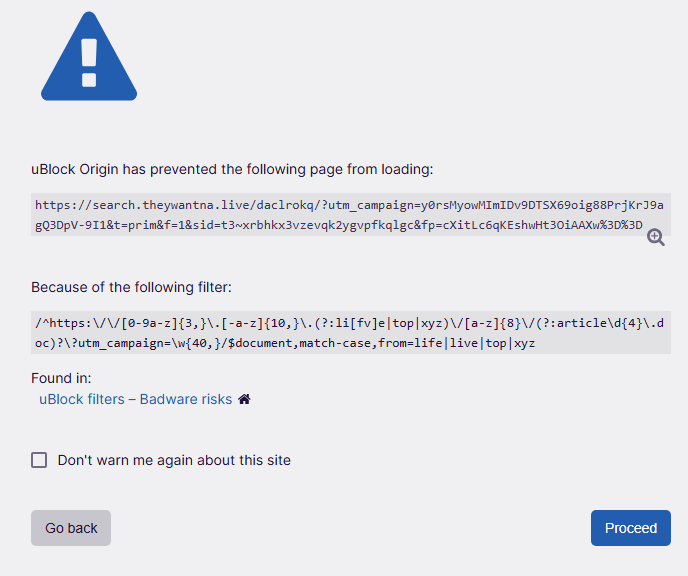
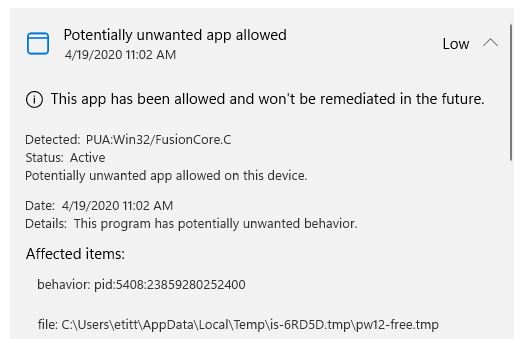
Whoa! I just got messages from a colleague on LinkedIn, and have confirmed for both that social media platform and Facebook, that something wicked this way comes. That is, it seems there’s a WordPress link access API hack that enables malicious redirection whenever a link compaction program calls my site for link info. You can see what this looks like in the lead-in graphic. To mangle Talking Heads my reaction is “That’s not my beautiful site! Those aren’t my URLs.” Ai-yi-yi!
Fixing WordPress Link Access API Hack
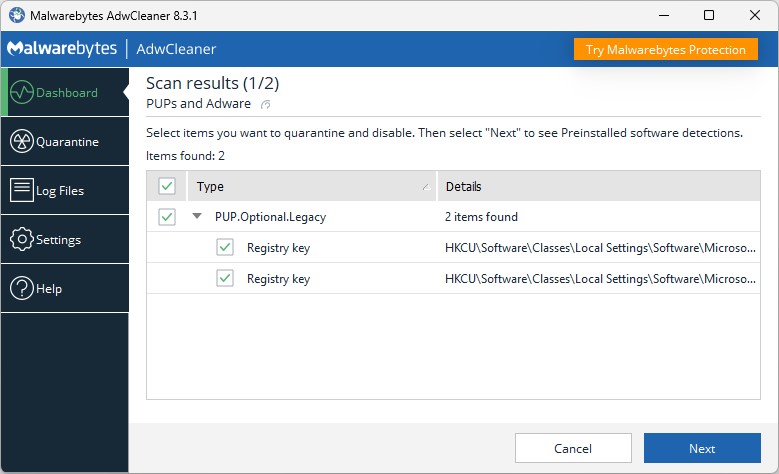
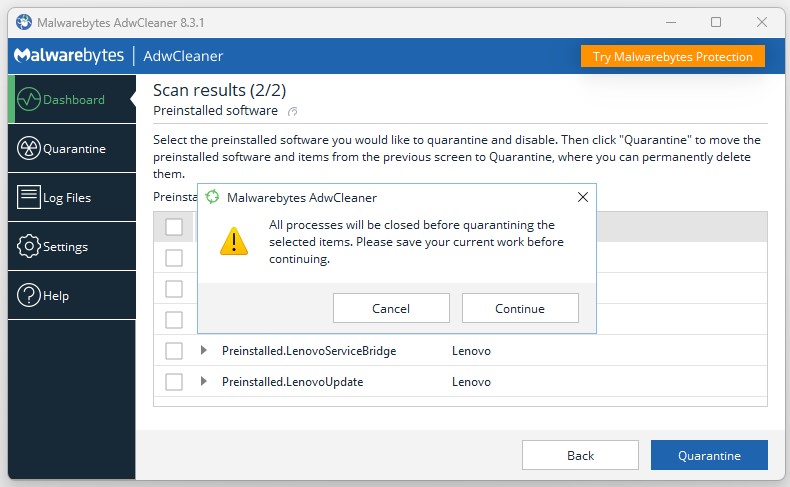
Scan, remove bad references. remove any suspect WordPress elements. Put a security scan service in place to prevent recurrences. That’s what my Web guy is working on right now. For whatever odd and obviously invalid reason, I thought my WP service already covered all these bases. Now that I know that’s untrue, it will get fixed as soon as that work gets done.
Wow! What an astonishing PITA for something so modest and focused. It seems that several configuration files got modified through a vulnerable plug-in and included references to malicious URLs as of 5/21. We’re changing all the passwords, fixing what’s wrong, and cleaning up the mess. I’m hopeful things will be back to normal by tomorrow.
Going forward, we’ve added explicit ongoing security scans, and regular reviews of software selections, patch levels, and protective software to the mix. Hopefully, this won’t happen again. But if you see something odd any time you access one of my posts or Web pages, do like MS MVP Simon Allison did, and let me know right away that something seems funny or broken. Every little bit of insight and info helps!
Note Added 6/5 2:40 PM
The URL/API portion of the site has been replaced, and no more malicious or suspect URLs get generated. The issue is apparently fixed, but we’re still scanning all files in the entire site to make sure no other unwanted content/malicious payloads are lurking anywhere. All’s well that ends well, but the road goes on forever and the party never ends…