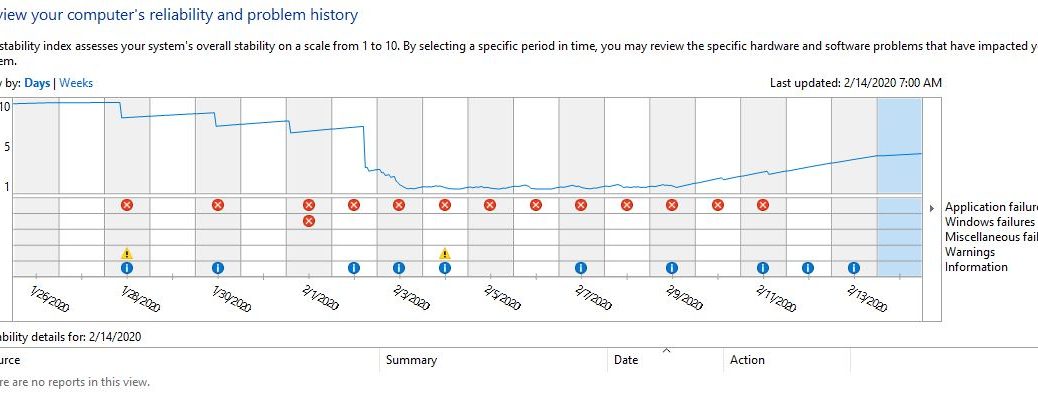
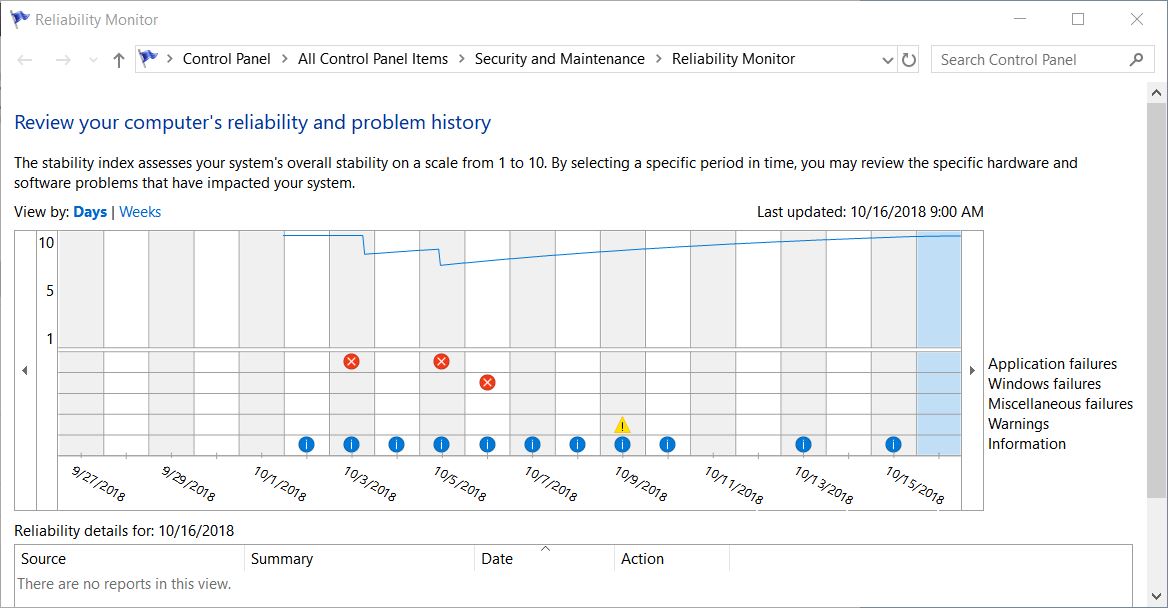
Over the past couple of weeks, I’ve been fighting some vicious Windows 10 issues. One of them manifested in the form of over 100 Outlook MoAppCrash errors related to WindowsCommunicationApps that check in with remote email servers. Those came at a rate of at least 5X daily. The other involved regular IAStorDataMgrSvc.exe errors, at the rate of at least one a day. Between the two, as the intro screencap shows, my system’s Reliability Index hit rock bottom 7 days in a row. But between using the Microsoft Support and Recovery Assistant (aka MS SaRA) and removing an unnecessary driver, I’ve been able to return my production PC to more or less normal operation. Hence this blog post’s title: MS SaRA + removing IRST restores Win10 stability.
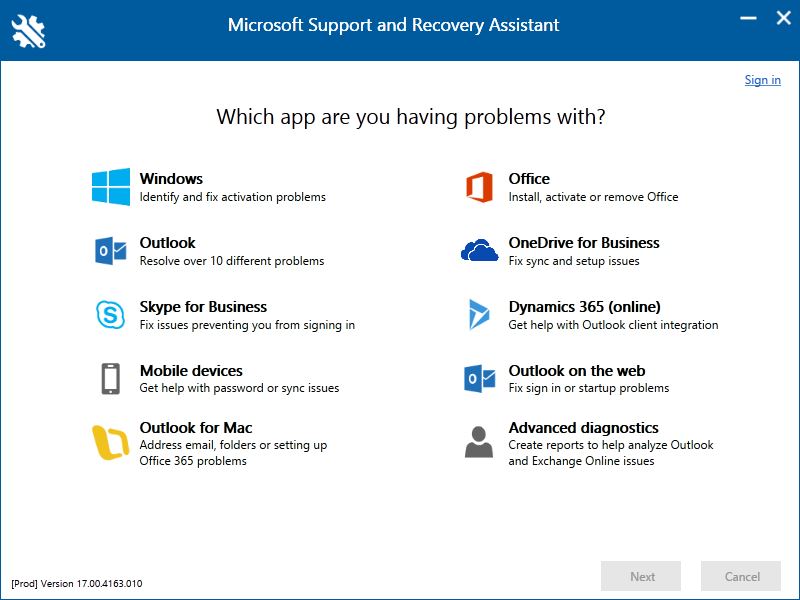
As SaRA’s home screen shows, it’s good for addressing a broad range of Windows problems. It definitely fixed my Outlook errors without too much muss or fuss.
[Click image for full-sized view.]
The Many Powers of SaRA
I hadn’t used SaRA much before (though I did have a copy in my utilities folder). But when I ran it, the software asked me to revisit its Download Center page to grab the latest version. I’m glad I did, because it’s added a lot of new Office and Outlook capabilities in this latest incarnation. And because that’s just what I needed, it was well worth doing. Having now used it on multiple occasions to fix a couple of trivial problems and this latest, more annoying and persistent Outlook issue, I can recommend it to Windows admins, power users, and even ordinary users alike. It should be part of any Windows user’s troubleshooting arsenal, as it is now part of mine (it goes way beyond Windows 10’s built-in Troubleshooters, available through Start → Settings → Update & Security → Troubleshoot). Grab a copy today.
Why Use the Intel IRST Drivers?
The ultimate source of my IAStor related “stopped working” error messages came from this folder:
C:\Program Files\Intel\Intel(R) Rapid Storage Technology\IAStorDataMgrSvc.exe
That’s what clued me in that the Intel Rapid Storage Technology (IRST) software was involved. Although IRST offers some modest performance boosts for SATA disks run independently, its biggest benefits come through its support for software-based RAID (Redudant Arrays of Inexpensive Disks). It turns out that for AHCI users who don’t have RAID disks, IRST is more or less optional. If you really want ALL the details on IRST drivers, versions, and access to nicely-modded alternatives, check out Fernando’s IRST Coverage at Win-RAID.com.
In my case, I decided to uninstall the whole environment because anything that causes errors but provides only modest performance gains is not something I want. Out it went. And, as the rising tide of the Reliability Index shows, taking care of both errors finally has things moving in the right direction. And that’s the way things go sometimes, here in Windows-World. I’m mildly pleased to see the system becoming more stable. Let me see it get back to a perfect 10, and I’ll be somewhat more pleased. Fingers crossed!