Yesterday, I noticed that both WinGet and PatchMyPC Home Updater hiccuped when trying to update CrystalDiskMark (8.0.6 to 9.0.0) and CrystalDiskInfo (9.6.3 to 9.7.0). This strange Crystal Dew World hiccup (that’s the home site for both apps) got me wondering if the developer had abandoned freeware versions of those tools for ad-driven (installer-based) or for-a-fee (MS Store) versions only. I’m please to report that my presumption was wrong, and new freeware versions for both programs are updating properly now.
What Caused This Strange Crystal Dew World Hiccup?
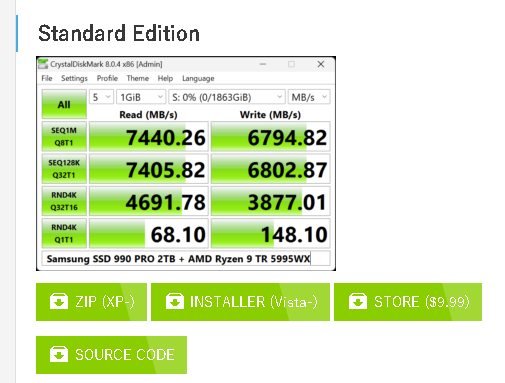
Apparently there was some delay between when the new version info got broadcast and when the Crystal Dew World website got updated. Indeed I saw web info (which serves as the lead-in graphic for the story) that led me to wonder if ad-driven (ZIP and Installer) or paid-for (Store) versions were the only remaining versions of CrystalDiskMark (CDM) and CrystalDiskInfo available.
This morning, however, when I went back to check again, things were different. I still see the same situation at Crystal Dew World (here’s a link to its CDM download which includes an installer named CrystalDiskMark9_0_0Ads.exe). But WinGet and PatchMyPC can both successfully upgrade these tools now (they threw “hash match fail” errors yesterday) and are proffering ad-free freeware versions that come from sourceforge (you can use WinGet Show CrystalDewWorld.CrystalDiskMark to reveal its database contents).
Updates Take Time to Propagate
I’ve seen similar things happen before — often, with MS facilities such as PowerShell and Windows Terminal — when an update emerges but packages and database contents don’t synch up. All in all, though, I’m glad that freeware, ad-free versions of these useful tools remain available. If they didn’t I’d have to find something else!
And, far too often, such things become necessary here in Windows-World. Not this time, apparently for CDM and CDI. Not yet, anyway… But the ad-oriented interface at Crystal Dew World strongly suggests it could happen if not now, perhaps later.