I read, with some amusement and a sense of inevitability this morning about a new Windows 11 feature. The latest Windows 11 Beta release (Build 22624.1610) supports presence sensing. Of course, special PC hardware augments are required. Apparently I have no PC new or advanced enough for this. Alas, no Windows 11 presence sensing for me!
What No Windows 11 Presence Sensing Means
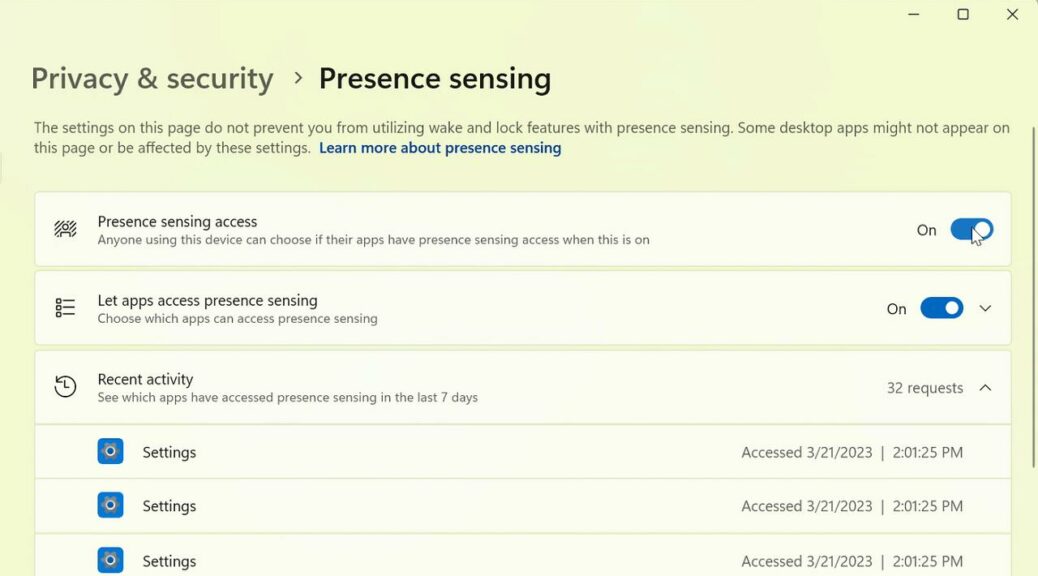
If I remember correctly the notion of “presence” comes from computer telephony. It means the user is present and in front of the device (PC, in this case). Presence data helps guide whether or not requests and data go to users who’ve registered for specific conferences, events, and so forth. If they’re present, they’re included; if not, they’re not. And also, presence detection can work with Windows Hello (via IR camera sensing) to determine if a user is in front of the PC, to handle login and access.
My Lenovo P16 Mobile Workstation is pretty good at visual recognition. It’s also a mid-to-late 2021 vintage PC. Thus, I’m surprised that it apparently does not support Windows Presence. How do I know? There’s no “Presence sensing” entry in Settings → Privacy & Security → entry on that PC (or any of my other machines). Sigh. Why is that when MS announces a new Windows feature, I either don’t have it in the build, or it’s not supported on my PC? I guess it’s just a consistent turn of (ill) fate for yours truly.
I’ll see if I can remember to ask Lenovo to make sure this feature is present (pun intended) on my next eval unit. If so, I can check it out. If not, I don’t think it will kill me.
And so it sometimes (or often) goes, here in Windows-World. Stay tuned for news about other new stuff I don’t (or can’t) have. I’ll keep you posted.