On January 18, I reported here that the Insider Team at MS renewed my Windows Insider MVP (WIMVP) status for 2021. Since that renewal came through, I’ve been keeping an eye on my daily activities and taking notes. Now, I’m prepared to share a mini-expose. It’s what I call “My Insider Preview working routine revealed,” as in the title for this story. I’ll explain what it means, what I do, and how much time it takes to stay involved in the program. Here goes…
Digging In: Insider Preview Working Routine Revealed
There are 5 major activities involved in the Insider Preview working routine, as far as I can tell. I’ll enumerate them first, then provide some details and ruminations.
- Dealing with Insider Preview releases
- Reporting on installation and use experiences
- Researching news and reports related to Insider Preview Releases
- Participating in the WIMVP community
- Raising awareness for Windows 10 plus related tools and utilities
1. Dealing with Insider Preview releases
I watch all the release channels — namely Dev, Beta, and Insider Preview, with at least 2 test machines devoted to each channel. Every time a new release comes out, I go through a specific drill, as follows:
- Download and install the release
- Observe any issues, hiccups or out-of-baseline behaviors during the install and initial trip to the desktop
- Perform post-install clean-up, which consists of deleting Windows.old, running file cleanup, and making a fresh backup of the new version in Macrium reflect
- Report on experience and findings at TenForums.com in the News forum and, if necessary, in the Installation and Upgrade forum
- Check Event logs and Reliability Monitor for out-of-the-ordinary stuff
- Report anything interesting or noteworthy to Feedback hub
As occasional updates to IP releases emerge, I repeat the steps above except for post-install clean-up, though I may run DISM /online /cleanup-image /analyzecomponentstore to see if any install packages need cleaning up in the wake of the new update. Sometimes they do, and sometimes they don’t.
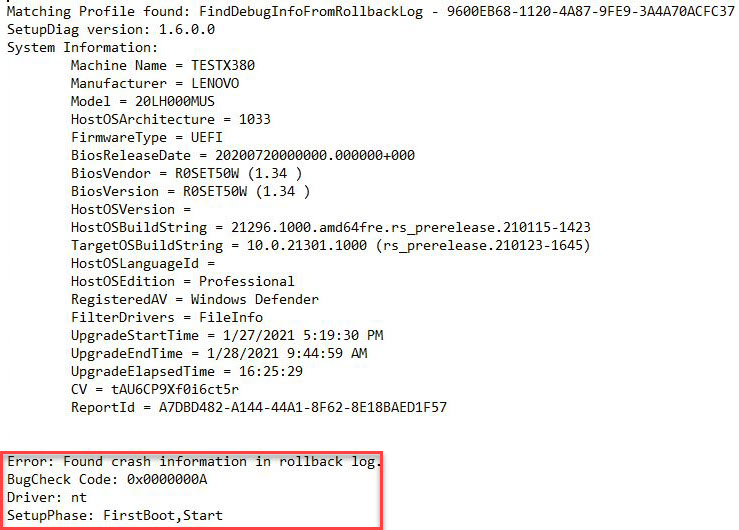
I do about 6 of these a week on average, where each one takes anywhere from 15 minutes to an hour if everything works as it should. Sometimes, troubleshooting can take an hour or more, as when troubleshooting installation failures. Right now, for example, I’m dealing with a Bug Check 0xA IRQL_NOT_LESS_OR_EQUAL stop error on Build 21301 on one of my test machines. I may not get this resolved until after dinner tonight because I have three deadlines to meet today (this article, a story for ComputerWorld, and a blog post for ActualTechMedia).
2. Reporting on installation and use experiences
Once I get the IP release installed and cleaned up, I start using it from time to time. As I observe its behavior and try out commands, programs, apps and utilities, I report any issues I encounter to Feedback hub. This depends a lot on my overall workload and may involve only 10 minutes on some days, and an hour or two on others. Varies a lot.
3. Researching news and reports related to Insider Preview Releases
I read the Windows 10 coverage on at least a half-dozen sites daily to keep up with current events, reported bugs and issues, emerging features and rumors of same. I also keep a partial eye on Microsoft business and tech news, as well as PC software and hardware industry news. This takes me at least an hour a day; longer if I get interested in something and start tracking stuff down. My daily visits include WinAero.com, Windows Latest, MSPowerUser, NeoWin, OnMSFT, Ghacks, ZDNet, Windows Central, and TenForums.com (where I try to read all new threads every day).
4. Participating in the WIMVP community
I belong to the WIMVP Yammer group, and scan its posts daily. We have weekly meetings to discuss Windows 10 topics which I sometimes attend (but not always). When we have online meetings — as we will later this morning — I try to attend those pretty regularly. I make a point of attending our conferences, and used to enjoy the physical ones. Now, like everybody else, I get what I can from their online/virtual counterparts, and look forward to when traveling for a real meet-up is once again possible. This takes me an hour or two a week on average, with 2-3 full days for conferences.
5. Raising awareness for Windows 10 plus related tools and utilities
I’m always on the lookout for good Microsoft-built or third-party tools, utilities, scripts, and whatnot. As I find them, I write about them in my daily reporting, and try to get articles placed to write about them in more detail and depth. You can get an inkling of what I do from my end-of-last-year story here Top 3 2020 Utilities. This is about the most fun I get to have in this role, but seldom takes more than an hour or two a week, sometimes less.
I also give an annual Windows 10 presentation at the Spiceworks SpiceWorld conference, and try to pick up other speaking and presenting gigs as they make themselves available. If you want me to talk about Windows 10 stuff at your conference and I don’t have a conflict, I’d be happy to oblige. Contact me through Ed Tittel Contact Info, where you’ll find an email form that goes straight into my inbox.