OK, then. I just struck a small lode while mining for Windows 10 gold. I found it in a Windows 10 Docs item named “Troubleshooting upgrade errors.” Therein, MS Docs names Windows 10 upgrade four phases. This document describes four phases during the upgrade process, and provides pointed troubleshooting suggestions and identifies useful error codes wherever it can. Good stuff!
If MS Docs Names Windows 10 Upgrade Four Phases, What Are They?
In the afore-linked Docs item, the four phases of Windows 10 Upgrade are named as follows:
Downlevel phase
This occurs while the old OS is still running (hence the name). This is the phase that runs right up until the initial reboot, at which point the old OS is no longer running. During this phase MS downloads all the pieces and parts it needs to perform the upgrade, so it’s apt to label this as an initial set-up and preparation phase. Errors that occur at this phase are most likely related to file access or download issues encountered as setup.exe attempts to pull all the pieces onto the target PC.
SafeOS phase
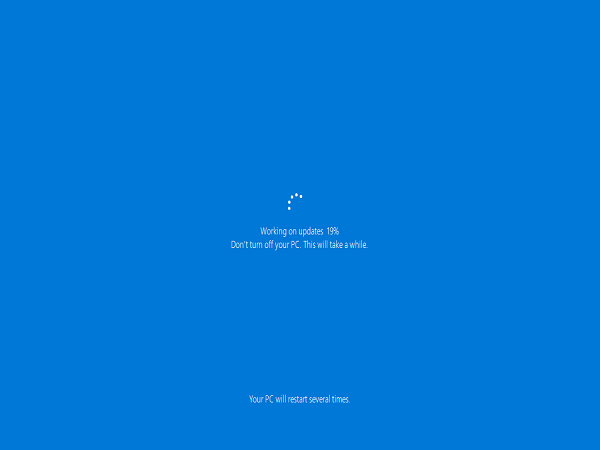
At this point you see something like the screencap shown in the lead-in graphic for this story. Following the initial reboot, Windows PE boots from the install image supplied as part of the source files for the upgrade. Those files might come from Windows Update, or an ISO obtained (and mounted) from the Media Creation Tool, Visual Studio downloads, or any number of other reputable Windows 10 image sources (Heidoc.net, UUPdump.ml, and so forth). Errors that occur at this phase at most likely device driver related.
First boot phase
About 30% into the “Working on updates” (SafeOS) phase, Windows 10 will reboot again to load key drivers for graphics and networking adapters or circuitry. Here again, driver issues are the most common cause of problems. Microsoft wisely advises those who encounter problems during this phase “[d]isconnect all peripheral devices except for the mouse, keyboard and display. Obtain and install updated device drivers, then retry the upgrade.”
Second boot phase
About 70% into the “Working on updates” phase, Windows 10 reboots one or more times as needed. Now it is running the new OS with its new drivers. When errors occur during this phase, they most commonly originate from anti-virus software or filter drivers. Key advice: “Disconnect all peripheral devices except for the mouse, keyboard, and display. Obtain and install updated device drivers, temporarily uninstall anti-virus software, then retry the upgrade.” This phase is sometimes called the OOBE boot phase, during which final settings are applied.
Those who make it through all four phases complete their successful upgrade when they go through (or bypass) the “Out-of-box” phase (“Hi! We’ve got some updates for your PC. This might take several minutes.”)
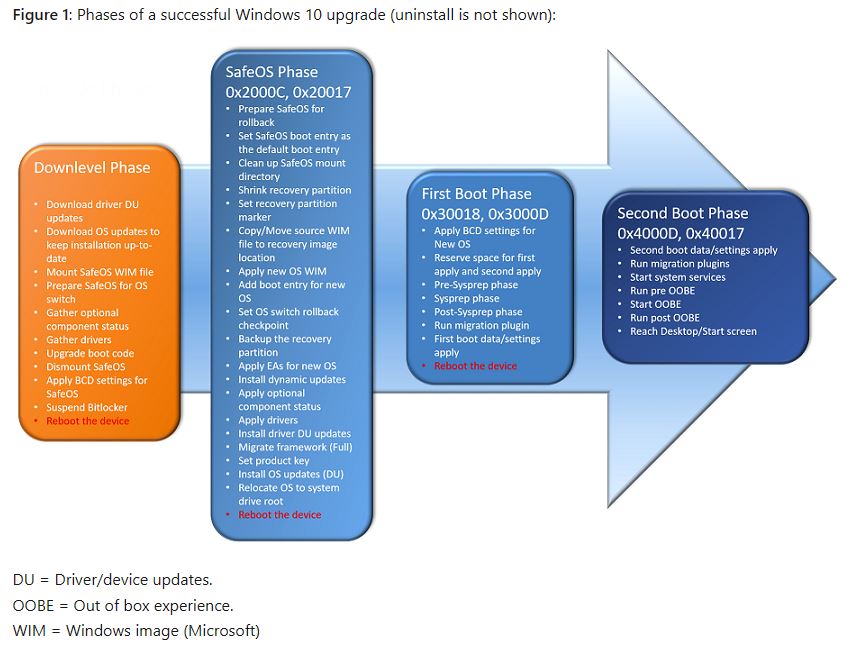
Here’s a helpful diagram of the process that MS provides in the afore-linked Docs file:
[Click image for full-sized view. Much more readable!]
Notice it provides ample technical details about what’s going on in each phase. IMO, this is the most informative element in the whole document. Definitely worth reading right away (and returning to when handling upgrade or clean install issues). Enjoy!